All Q-Day, Y2Q Posts
-
Q-Day

Q-Day Knowledge Center & Q-Day Framework and Estimator
Q-Day Knowledge Center - Your complete guide to understanding, forecasting, and preparing for quantum decryption risk.
Read More » -
Q-Day

Forget Q-Day Predictions – Regulators, Insurers, Investors, Clients Are Your New Quantum Clock
Whether you personally believe Q-Day will come in 5 years or 50, the world around you isn’t taking chances - and neither can you. As a CISO, you’re now being implicitly (and sometimes explicitly) told by every corner of your ecosystem that quantum preparedness is mandatory. Regulators demand it via hard deadlines. Key clients and partners demand it in contracts and RFPs. Insurers will soon…
Read More » -
Q-Day

How You, Too, Can Predict Q-Day (Without the Hype)
For three decades, Q-Day has been “just a few years away.” I want to show you how to make your own informed prediction on when Q-Day will arrive. Counting physical qubits by itself is misleading. To break RSA you need error‑corrected logical qubits, long and reliable operation depth, and enough throughput to finish within an attack‑relevant time window.
Read More » -
Post-Quantum, PQC, Quantum Security
CRQC Readiness Benchmark vs. Quantum Threat Tracker (QTT)
I will try and compare my proposed CRQC Readiness Benchmark with QTT, highlighting fundamental differences in methodology, assumptions, and philosophy, all in an effort to clarify how each approach informs our understanding of the looming “Q-Day.” The goal is to articulate why my benchmark and QTT produce different outlooks (2030s vs. 2050s for RSA-2048), and how both can be used together to guide post-quantum readiness.
Read More » -
Q-Day
The Trouble with Quantum Computing and Q-Day Predictions
The trouble with quantum computing predictions so far has been that too many have been more speculation than science, more influenced by bias than by balanced analysis. We have the tools and knowledge to do better. By embracing a data-driven, scenario-based approach, we can turn timeline forecasting from a source of confusion into a valuable planning aid.
Read More » -
Q-Day
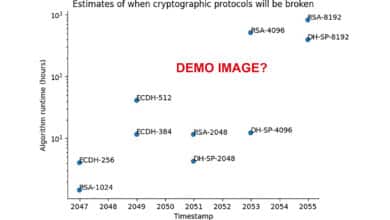
Quantum Threat Tracker (QTT) Review Praising the Tool Questioning the Demo
The Quantum Threat Tracker (QTT) is a newly released open-source tool by Cambridge Consultants and the University of Edinburgh that aims to forecast when quantum computers will break today’s encryption. It combines quantum resource estimation (using optimized variants of Shor’s algorithm) with hardware development roadmaps to predict when cryptographic protocols will be broken. In other words, QTT estimates how many qubits and runtime are needed…
Read More » -
Post-Quantum, PQC, Quantum Security
CRQC Readiness Benchmark – Benchmarking Quantum Computers on the Path to Breaking RSA-2048
Benchmarking quantum capabilities for cryptography is both critical and challenging. We can’t rely on any single metric like qubit count to tell us how near we are to breaking RSA-2048. A combination of logical qubit count, error-corrected circuit depth, and operational speed must reach certain thresholds in unison. Existing benchmarks – Quantum Volume, Algorithmic Qubits, etc. – each address parts of this, but a CRQC-specific…
Read More » -
Q-Day
Q-Day Revisited – RSA-2048 Broken by 2030: Detailed Analysis
It’s time to mark a controversial date on the calendar: 2030 is the year RSA-2048 will be broken by a quantum computer. That’s my bold prediction, and I don’t make it lightly. In cybersecurity circles, the countdown to “Q-Day” or Y2Q (the day a cryptographically relevant quantum computer cracks our public-key encryption) has been a topic of intense debate. Lately, the noise has become deafening:…
Read More »