G7’s Post‑Quantum Roadmap: Preparing the Financial Sector for a Quantum-Resilient Future
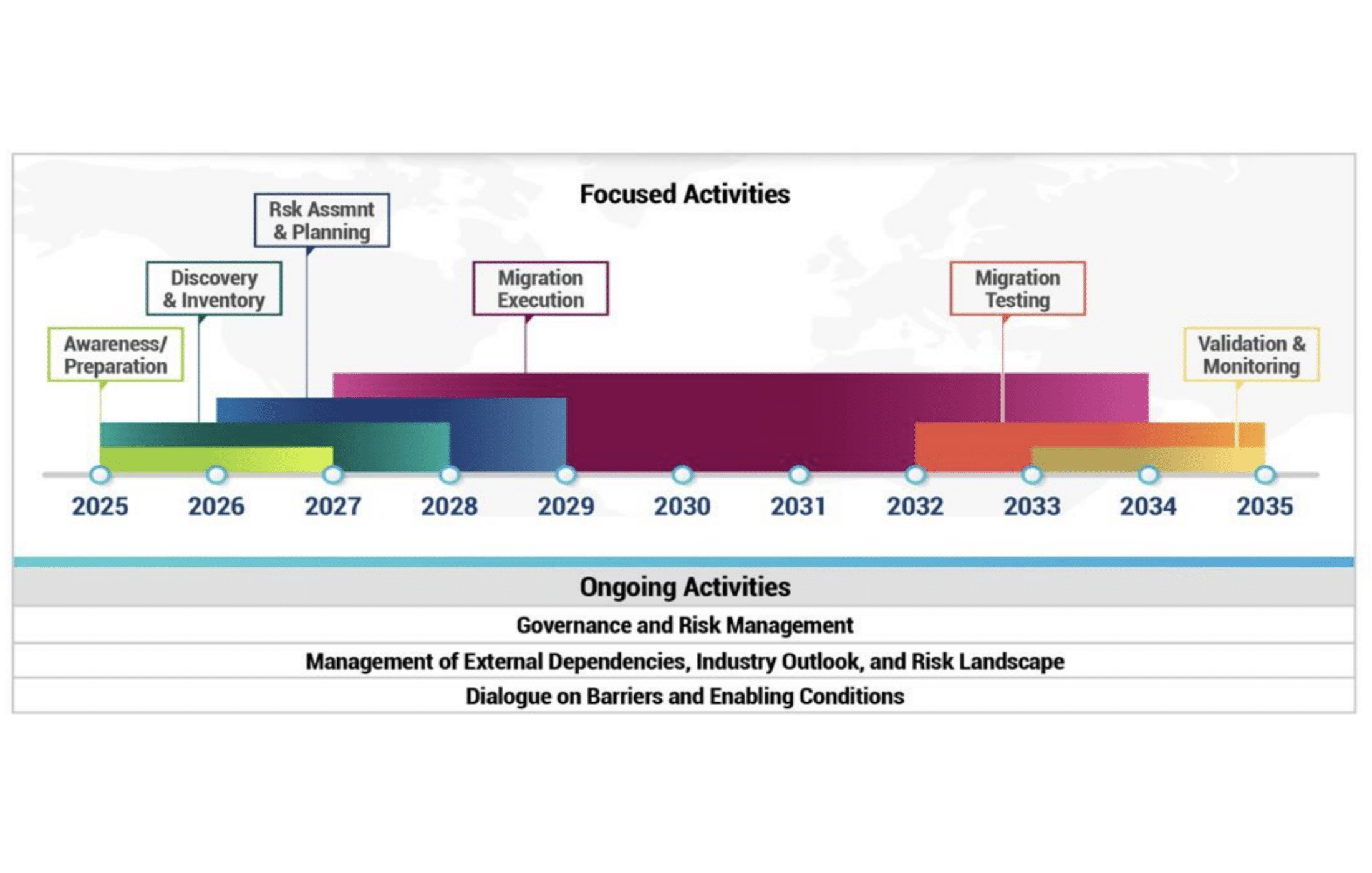
Table of Contents
12 Jan, 2026 – The G7 Cyber Expert Group (CEG) – an international team of cybersecurity authorities co-chaired by the U.S. Treasury and the Bank of England – issued a landmark roadmap for the financial sector’s transition to post-quantum cryptography. This high-level plan, formally titled “Advancing a Coordinated Roadmap for the Transition to Post‑Quantum Cryptography in the Financial Sector,” is aimed at banks, financial market infrastructures, regulators, technology vendors, and other key players across G7 economies. Its message is clear: the clock is ticking on today’s encryption. Quantum computing advances could render the cryptographic foundations of modern finance obsolete within the next decade. The G7 is urging a proactive, coordinated shift to quantum-resistant security now – before quantum-capable adversaries can exploit the gap.
What is the G7 CEG and why does its roadmap matter?
The G7 Cyber Expert Group was established in 2015 to advise G7 finance ministers and central banks on cybersecurity issues and to coordinate policy across major economies. Its new roadmap addresses the looming risk of cryptographically relevant quantum computers (CRQCs) – powerful quantum machines that could break the encryption algorithms underpinning financial transactions and data privacy.
While such CRQCs do not exist at scale yet, the threat is not theoretical. Experts widely project that a sufficiently advanced quantum computer capable of cracking today’s public-key encryption (like RSA and elliptic-curve algorithms) could be developed by the early-to-mid 2030s. In the financial world, that timeline is uncomfortably close. Data breaches are already occurring under a “harvest now, decrypt later” model, where attackers steal or intercept encrypted information today with the intent to decrypt it once quantum capabilities emerge. This creates an immediate risk for long-lived data – think of trade secrets, health records, loan documents, or any sensitive financial contracts that need to remain confidential for decades. Unless we start protecting such data with quantum-resistant methods now, a quantum-equipped adversary could someday pull those secrets out of historical traffic or archives.
PQC to the rescue
Post-quantum cryptography (PQC) is the proposed solution. PQC refers to a new generation of cryptographic algorithms designed to withstand attacks from quantum computers. Over the past few years, researchers and standards bodies (like NIST in the U.S.) have been evaluating and standardizing these quantum-resistant algorithms. The G7’s roadmap provides guidance on moving to quantum‑resilient encryption – in other words, deploying PQC – across the global financial system in a safe and coordinated way.
Importantly, the roadmap also emphasizes cryptographic agility. Cryptographic agility is the ability to switch out cryptographic algorithms and protocols with minimal disruption as threats and technologies evolve. In practice, this means building systems that aren’t locked into a single encryption scheme but can be updated to new algorithms as needed. The G7 highlights agility because the coming PQC transition “will certainly not be the last one required” in our lifetimes. In short, the goal is not only to swap in quantum-safe algorithms, but to ensure the financial sector can adapt again in the future, should new cryptographic weaknesses or breakthroughs emerge.
Inside the G7 Roadmap: A Coordinated Path from 2026 to 2035
The G7’s roadmap is meant to guide the entire financial sector – not just banks, but also regulators, fintech firms, cloud providers, payment networks, cryptographic technology vendors, and others – toward a common timeline and set of practices for quantum readiness. It does not impose hard requirements or regulatory mandates; rather, it offers a framework and timeline to inform planning in both public and private sectors. The idea is to ensure everyone is moving in the same direction and roughly the same time window, thereby maintaining interoperability and avoiding weak links.
Who is it for?
In a word, everyone in the financial crypto ecosystem. The roadmap acknowledges that large banks and market utilities depend on many third-party providers for cryptographic services. A small credit union might rely on a cloud vendor for its IT, or an exchange might rely on hardware security module (HSM) vendors for encryption. The guidance is therefore directed at financial institutions of all sizes, financial regulators and authorities, critical service providers (like cloud and payment processors), infrastructure operators, software and hardware vendors, national cyber agencies, and standard-setting bodies. By casting a wide net, the G7 is reinforcing a key point: no single institution can achieve quantum resilience in isolation. It’s a collective effort across interdependent networks.
Timeline and milestones
Perhaps the most striking part of the G7 roadmap is the timeline it lays out for the quantum transition. The group assessed expert opinions and national guidance and landed on a challenging but prudent timeframe for the whole sector to become quantum-safe. Specifically, the roadmap points to 2035 as an overall target date by which the migration to quantum-resistant cryptography should be largely complete across the financial system. This aligns with many experts’ predictions for when a CRQC might realistically be developed, and it matches strategic timelines being discussed by standards bodies like NIST. By 2035, in other words, the G7 expects that government systems, private financial institutions, and critical providers worldwide should be using post-quantum encryption as the norm.
Because 2035 is still a rough estimate (not a guaranteed “Q-Day”), the roadmap wisely builds in flexibility. It notes that target dates may shift if the threat landscape changes – for example, if quantum scientific progress accelerates unexpectedly, the timeline would need revising. But using 2035 as a planning beacon is useful to rally efforts. To manage risk in the interim, the roadmap recommends a risk-based sequencing of migration. Not all systems are equally critical or equally exposed. The guidance suggests prioritizing the most critical or sensitive systems earlier, aiming for quantum-safe solutions in those areas by around 2030-2032. Getting the highest-value crown jewels secured by the early 2030s provides a buffer against “downside risk,” in case a viable quantum attacker arrives sooner than expected. Less critical systems could follow on a slightly longer schedule. This dual-track approach – critical systems first, secondary systems later – reflects a consensus across G7 countries that early 2030s is a prudent target for core financial infrastructure to be quantum-resistant.
It’s important to stress that these dates are not hard deadlines or regulatory requirements at this point. The G7 roadmap is non-prescriptive; it offers a scenario for planning rather than a mandated schedule. Each organization is free to adapt the timelines based on its own risk assessments, the complexity of its tech environment, and the evolving maturity of PQC solutions. That said, having a common horizon (2030-2035) is immensely helpful for coordination. It means, for example, that if a bank is selecting a new vendor today, it can demand that the vendor’s products will support PQC well before 2035. Or regulators can start thinking about supervisory expectations that by the mid-2030s, financial institutions should have completed this transition.
Phased migration approach
The G7 roadmap outlines a multi-phase journey for organizations to follow on the road to quantum safety. This isn’t a simple “flip the switch” upgrade – it’s a gradual process that will span years. In broad strokes, the roadmap’s phases include:
- Awareness and preparation: Establishing executive-level understanding of the quantum risk and setting up a program for post-quantum transition. This means getting buy-in from leadership (boards and C-suites) that quantum security is a strategic priority, not just an IT curiosity. Many firms are still in this stage in 2026 – educating stakeholders and securing budget for what will be a long project.
- Discovery and inventory: Cataloguing all the cryptography in your organization and in your third-party dependencies. You can’t fix what you don’t know you have. This involves creating a cryptographic inventory or bill of materials: identifying everywhere you use encryption or digital signatures, all the algorithms, key lengths, and protocols in play. It also means mapping out which vendors or partners you rely on for cryptographic functions (e.g. cloud services, payment networks) so you know who else needs to be part of your transition plan. Many in the industry are surprised at how ubiquitous cryptography is – it’s woven through every application and network, often in layers of legacy systems. This discovery phase can be labor-intensive, but it’s foundational.
- Risk assessment and planning: Using the inventory to assess which systems and data are most at risk and prioritizing them. For instance, a trading platform that secures transactions with RSA might be deemed critical to upgrade sooner than an internal HR system. In this phase, organizations develop a concrete migration roadmap (specific to themselves) and ideally coordinate that plan with sector-wide timelines. Plans should consider not just technology, but also process and policy changes (for example, updating key management practices for larger PQC keys, or planning customer communication if needed).
- Migration execution: Deploying quantum-resistant solutions in a phased manner. Many experts expect an interim period where “hybrid” cryptography is used – combining classical and post-quantum algorithms – to maintain compatibility while adding quantum protection. Execution should start with pilot implementations in less critical systems to gain experience, then move to critical systems once confidence is gained. The G7 emphasizes that this stage must be done carefully; replacing cryptography is akin to performing open-heart surgery on the digital infrastructure of a bank. One cannot simply rip out RSA and drop in a new algorithm without extensive testing. Indeed, the roadmap explicitly cautions that migrating to PQC is not a routine software patch, but a fundamental re-engineering of security architecture that will take years to complete safely.
- Migration testing and validation: As new quantum-safe systems come online, they need thorough testing – not only within an institution but across the broader ecosystem. Think of processes like inter-bank payments or secure messaging between institutions: both sides (and the networks between) must be quantum-safe for the whole transaction to be secure. The roadmap envisions industry-wide resilience exercises and interoperability tests to ensure that the new cryptographic tools work in practice and that any weaknesses are discovered before a real adversary finds them. Regulators and industry groups may help coordinate these sector-wide tests.
- Ongoing monitoring and adaptation: Even after a successful migration, the work isn’t over. The final phase is about institutionalizing cryptographic agility – continuously monitoring the threat landscape and updating cryptography as needed. Security teams will need to keep an eye on emerging cryptographic standards (PQC is still evolving) and on quantum advancements, ready to pivot if, say, one of the chosen algorithms is later found to have a flaw. In essence, this phase means treating cryptography as a living system that requires upkeep, not a “set-and-forget” element. Organizations should incorporate PQC readiness into their ongoing risk management and incident response planning.
Throughout these phases, the G7 roadmap stresses collaboration and communication. Firms are encouraged to share lessons learned, tools, and even jointly develop standards or best practices, so that less-resourced institutions (which may have higher vendor dependency) are not left behind. The roadmap explicitly calls out the danger of fragmented approaches – if each firm goes its own way, the overall financial system could end up with weak links. Instead, harmonization (backed by standard protocols and coordinated timelines) will ensure that, for example, clearing houses, exchanges, and banks are all on the same page. Notably, the G7 also pledges to work closely with international standard-setting bodies and industry forums to drive this alignment.
From Roadmap to Reality: Gaps, Agility, and Next Steps
The G7’s roadmap is an important blueprint, but what does it mean in practice for financial institutions? In this section, we’ll analyze what the roadmap gets right, where challenges remain, and what steps organizations should be taking today to stay ahead.
A much-needed wake-up call – now make it actionable
One thing the roadmap clearly gets right is the tone of urgency and the high-level buy-in. By having the G7 finance authorities endorse this message, it signals to CEOs and boards that quantum risk is real and demands attention (it’s not just a tech issue for the IT department). As the CEG co-chairs put it, quantum encryption-breaking capability is a “significant risk to the safety and soundness of our financial ecosystem” that we must address together. This kind of top-down recognition is critical; without it, allocating budget and resources to a multi-year crypto-migration program would be very difficult. The roadmap also wisely frames the issue as systemic and collective: it’s about shoring up the entire financial sector, not gaining a competitive edge. In that sense, the G7 document serves as a rallying cry and reference point.
However, the flip side of being non-prescriptive is that the roadmap stops short of concrete mandates. It’s guidance, not law. One gap or risk here is that without regulatory compulsion or detailed requirements, some organizations may procrastinate. The roadmap provides a when and what at a high level, but not the how – the heavy lifting of execution is left to each institution. Banks that lack cryptographic expertise might be unsure where to start, or might underestimate the effort and think “2035 sounds far off.” In reality, a full migration can easily take 5-10 years for large enterprises, as anecdotal evidence from early movers suggests (some sectors like telecom have been grappling with this for years already). So a key message for financial firms is: don’t let the absence of a formal rule lull you into inaction. Waiting for regulators to eventually require PQC could put you behind the 8-ball, especially given the long lead times. Forward-looking institutions will treat the G7 timeline as a de facto directive and begin the transition now, using the roadmap as a checklist.
Data confidentiality lifetimes – know your risk horizon
An area of insight the roadmap touches on (and that organizations should scrutinize) is the concept of data confidentiality lifetime. Not all data is equal in how long it needs to remain secret. For example, a stock trade might only need confidentiality for a few hours (until it’s settled), whereas personal customer information or payment card details might need to stay encrypted for years, and certain banking records or intellectual property might be sensitive for decades. Each firm should assess how long each category of data must remain secure and compare that to the quantum timeline. If you identify information that still needs to be confidential in 2030 or 2040, that data is already in the quantum risk window today. Any such long-lived data encrypted with vulnerable algorithms is effectively on borrowed time. The G7 roadmap underscores this by pointing out that data can be snatched now and decrypted later when the tech matures. The practical takeaway: prioritize quantum-safe measures for data with long confidentiality requirements. This might involve re-encrypting archives with PQC or introducing quantum-safe encryption for communications that carry long-term secrets (for instance, VPN links that protect years’ worth of sensitive transactions). It also means revisiting your data retention policies – if you don’t actually need to keep certain sensitive data for 20 years, don’t! Minimizing the amount of “high-risk longevity” data can reduce your exposure.
Third-party and vendor dependencies – no one goes quantum-safe alone
The financial sector is highly interconnected and also heavily outsourced in certain areas. Many institutions rely on vendors for critical technology – be it the core banking software, cloud-based data centers, encryption libraries, or payment processing services. The G7 roadmap rightly highlights the risk here: smaller organizations, in particular, will depend on their vendors to deliver quantum-resistant solutions in a timely manner. If those vendors drag their feet, their clients can’t move forward, creating a chain of vulnerability. A striking example is how much of global financial traffic runs over protocols and networks managed by third parties (SWIFT, credit card networks, cloud infrastructure like AWS or Azure). If those aren’t quantum-safe, individual banks cannot unilaterally fix the issue. Therefore, an immediate step for financial institutions is to engage with your vendors and service providers. Ask them for their PQC transition roadmap – do they have one? When will their products support PQC algorithms? The G7 task force found that limited transparency into vendor plans is a real barrier and urges obtaining detailed vendor roadmaps as part of transition planning. In practice, this might mean updating procurement requirements to favor vendors who are proactive about quantum security, and possibly pressing industry groups to develop certification or standards for “quantum-ready” products. Regulators can assist by gathering information from major service providers (like cloud companies) and sharing timelines so that financial firms can plan accordingly. The bottom line is that quantum resilience has to be a team sport: your security is only as strong as the weakest link in your supply chain.
From PQC migration to true cryptographic agility
Many institutions might view the coming transition as a one-time project: swap out RSA/ECC for the new PQC algorithms and you’re done. The G7 roadmap takes a more forward-looking stance, pushing organizations to strive for cryptographic agility rather than a check-the-box replacement. What’s the difference? Think of it this way: transitioning to PQC is like installing a new lock on your door because a new kind of burglar is coming. Cryptographic agility is like redesigning the door such that locks can be changed anytime easily. It means building an environment where changing cryptographic primitives – whether due to a broken algorithm, a better standard, or a new threat – can be done with relative speed and minimal upheaval. This has not been the norm historically; many financial institutions today are running systems with hard-coded cryptography from decades past, precisely because changing it is so arduous. We now have an opportunity to future-proof. As NIST noted (and the G7 echoed), the post-quantum migration “will certainly not be the last one required”. New mathematical insights or even farther-future technologies could again threaten our cryptosystems.
So, as firms implement PQC in the coming years, they should also invest in architectures and processes that make the next crypto swap easier. Practically, this could involve using abstraction layers for cryptographic operations (so that you can change an algorithm in one central place instead of rewriting dozens of applications), embracing standards that support algorithm agility (for example, protocols that allow negotiation of new cipher suites), and maintaining an up-to-date cryptographic inventory (so you always know what you’re using and where). True agility also has an organizational component: it means having governance in place – clear ownership of cryptographic systems and a habit of regular updates. The G7 roadmap’s focus on agility is a call to avoid getting complacent after this transition; instead, embed cryptographic adaptability as a permanent discipline. Financial firms that heed this will not only ease the PQC rollout but will be much more resilient against whatever cryptographic surprises the future holds.
What should financial institutions be doing now?
With the quantum threat timeline uncertain but looming, the worst mistake would be to treat this as “someone else’s problem” or something to worry about in five years. There are several concrete steps that organizations, even those new to quantum security, should initiate immediately:
- Raise awareness at the top and secure buy-in: If you haven’t already, brief your executive team and board about CRQCs and the “harvest now, decrypt later” issue. Use the G7 statement and other authoritative sources as supporting evidence to make the case. This is critical for getting the necessary resources. Emphasize that this is a strategic risk management issue, not just an IT upgrade. The fact that G7 finance ministries and central banks are involved underscores the systemic importance.
- Start your cryptographic inventory: Many organizations will find this to be an eye-opening exercise. Assemble a team (with both security and IT architecture expertise) to map out all uses of cryptography in your environment. Identify software, hardware, and services that implement encryption, key exchange, digital signatures, and so on. Don’t forget less obvious areas: employee single sign-on systems, VPNs, stored data backups, and partner connections. Also, catalog the cryptographic libraries and modules in use – are you using OpenSSL, BouncyCastle, a cloud KMS, etc., and what algorithms do they support? This inventory forms the bedrock of all further planning. Larger institutions might leverage automated tools to scan code and configurations for crypto usage. Smaller firms might rely on vendor documentation. It can take time, so start early.
- Assess and prioritize: Once you see the crypto landscape, perform a risk assessment. Which encrypted data, if stolen today, would still be sensitive in 5, 10, 15 years? Which systems are most critical to protect (due to high impact or regulatory importance)? Also consider where you have the most exposure – for example, internet-facing systems using RSA/ECDSA-based TLS are a known future risk vector. This assessment will inform an internal roadmap of what gets upgraded first. It might be wise to tackle a non-critical system as a pilot to gain experience with PQC integration, but in parallel begin designs for retrofitting crypto in critical systems by the early 2030s. Many organizations adopt a dual-track approach: an R&D track to experiment with new algorithms in test environments now, and a production track to schedule phased upgrades for each system over the coming years.
- Engage with the ecosystem: As stressed, you’re not doing this alone. Participate in industry working groups on post-quantum transition if possible (many countries have forums or the FS-ISAC might have interest groups). Talk to your key technology providers about their support for PQC – for instance, ask your cloud provider when they will offer quantum-safe VPN or storage encryption options, or ask your network hardware vendor about PQC in TLS and IPsec. Share what you learn with your peers, and learn from their trials as well. The G7 roadmap encourages exactly this kind of cross-organization dialogue to avoid reinventing the wheel and to ensure everyone has solutions available when needed. Regulators too will likely facilitate information-sharing (some have published guidelines already). Staying plugged in will help you align your efforts with emerging standards and not get caught off guard.
- Build cryptography into resilience planning: Most financial firms regularly conduct disaster recovery and cyber incident simulations. It’s time to add quantum failure scenarios to that list – for example, what if in 2030 an adversary suddenly demonstrated the ability to break RSA-2048? How quickly could you swap in a safe algorithm? Treat this as part of operational resilience. Some organizations are even practicing “crypto agility drills,” switching out a TLS certificate or cryptographic module in a test system to see what breaks. That kind of muscle memory will be invaluable. Your goal should be that by the time PQC is standardized and products are available, your organization is not only ready to deploy them, but also capable of doing so smoothly.
In summary, the G7’s coordinated roadmap is both a call to action and a reassurance. It’s a call to action because it makes plain that the era of quantum risk is approaching and that the financial sector must mobilize now to defend the security of our data and transactions. But it’s also a reassurance in that it provides a clear, common direction: you are not navigating this transition alone or blindly. By following the roadmap’s guidance – planning for 2030-2035, prioritizing wisely, collaborating widely, and striving for true cryptographic agility – financial institutions can move from reactive patching to a proactive, systemic defense.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.



