Crypto Agility Goes from Buzzword to Blueprint – NIST Releases “Considerations for Achieving Crypto Agility”
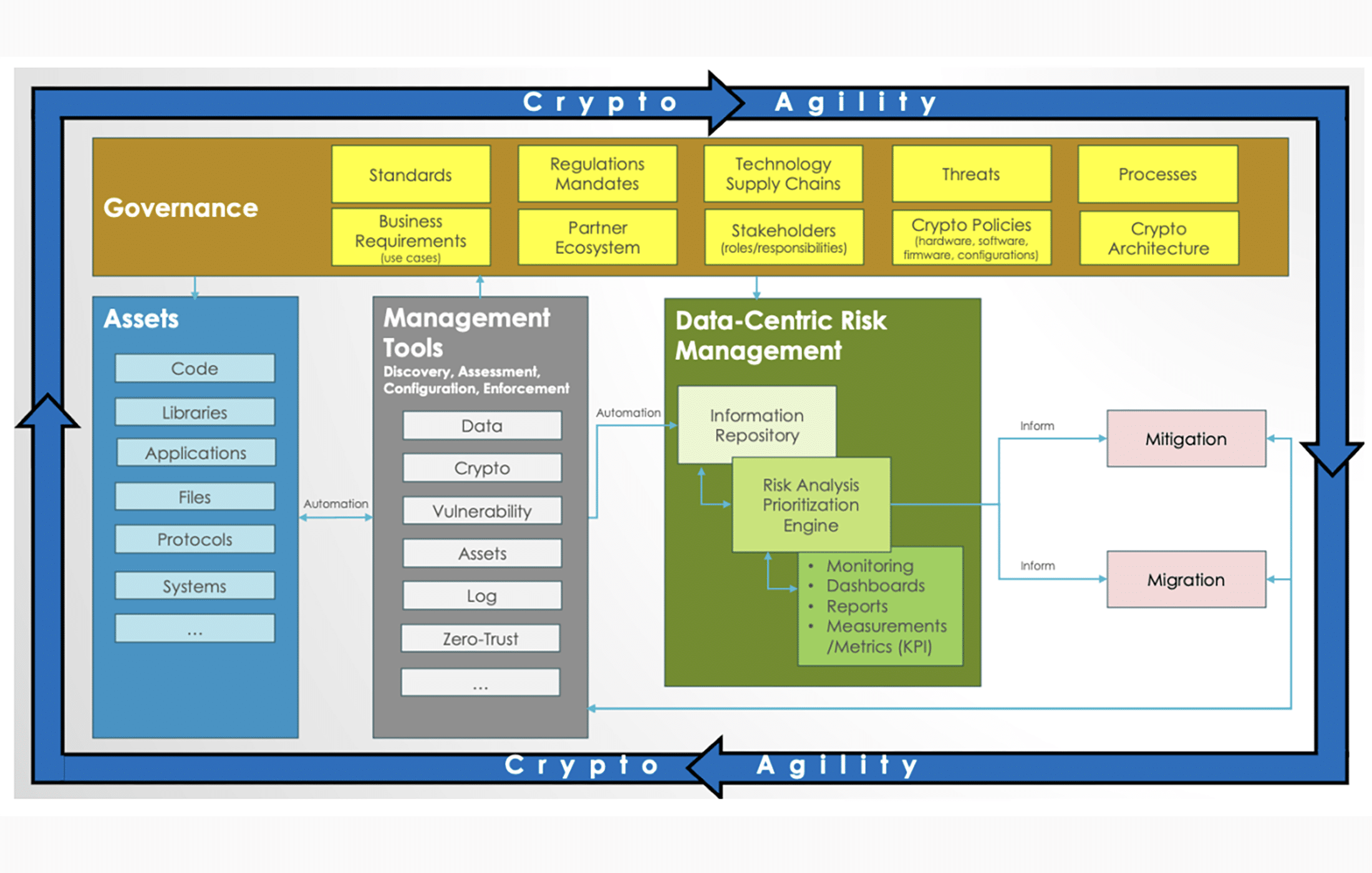
Table of Contents
21 Dec 2025 – NIST published the final version of the Cybersecurity White Paper (CSWP) 39 – “Considerations for Achieving Crypto Agility: Strategies and Practices.” CSWP 39 elevates cryptographic agility from an oft-cited buzzword to a design imperative for both government and industry. The message is clear: organizations must be able to adapt their cryptography on the fly without breaking systems, treating agility as a foundational requirement rather than an optional enhancement.
In NIST’s own words, crypto agility is now “a key practice that should be adopted at all levels, from algorithms to enterprise architectures”. This reframing transforms cryptography from a narrow technical concern into a core element of business resilience and risk management. The final NIST guidance is a policy and architecture blueprint that will reshape how cryptographic infrastructure is governed across federal agencies and the private sector.
From Reactive Migration to “Planned Agility”
Historically, most organizations have handled cryptographic transitions in a reactive, ad-hoc way – changing algorithms only when absolutely forced, often at great expense and risk. NIST CSWP 39 pointedly contrasts this past with a future of planned agility. One of the paper’s central themes is that crypto transitions (like the ongoing post-quantum migration) should not be treated as one-off, emergency projects, but rather anticipated as a continuous process. In fact, CSWP 39 introduces a maturity model for crypto agility, ranging from “unstructured and unplanned” practices at the low end to adaptive programs fully integrated into enterprise risk management at the high end. The goal is to climb from a world where “algorithms were hard-coded, keys scattered, and updates treated as one-time fixes” to one where agility is baked into governance. This notion of “planned agility” means building systems that are designed to change. NIST’s strategic plan explicitly urges executives to integrate crypto agility into corporate risk frameworks and transition plans, rather than wait for crises. In short, the paper flips agility from a reactive scramble to a proactive posture.
Key Pillars: Modularity, Abstraction, and Policy-Driven Control
What does crypto-agile design look like in practice? NIST’s guidance drills into several technical levers and architectural principles to enable agility:
Modularity is paramount – cryptographic algorithms should be cleanly separable from application logic, so they can be swapped out like plug-and-play components. For example, a security protocol implementation should be modular enough to accommodate new cipher suites easily. Likewise, operating systems and hardware should use updatable crypto modules (where feasible) or pluggable accelerators. Abstraction via standard APIs is another pillar: applications should request cryptographic services (e.g. “encrypt this data”) through well-defined crypto libraries or interfaces, rather than calling specific algorithms directly. A cryptographic API acts as a layer of insulation – the same API call can invoke AES today and a quantum-safe cipher tomorrow, without the application needing to change. NIST even floats the idea of a common cryptographic API across the industry to further standardize this abstraction layer for agility.
Equally important is policy-mechanism separation – the paper suggests cryptographic choices be driven by external policy settings rather than hard-coded in software. In practice, this means cryptography should be configurable via machine-readable profiles or management consoles. If a hash algorithm becomes disallowed, an admin should be able to update a policy file or setting to enforce that across systems, instead of developers rewriting code. CSWP 39 describes how cryptographic security policies can be centrally defined and then translated into “technology-specific, machine-consumable configuration profiles” that systems enforce with automated tools. This allows algorithm restrictions or additions to roll out quickly as configurations, not code changes. For instance, many protocols already let policy dictate cipher suite preferences; NIST stresses that organizations leverage these features to disallow vulnerable algorithms in a timely fashion while having newer options ready. In essence, modular code, abstracted APIs, and policy-driven controls form a trifecta enabling “agility by design” – cryptography becomes a flexible, managed system property rather than a static implementation detail.
Cryptographic Bill of Materials (CBOM) and Visibility
Another notable contribution is NIST’s emphasis on visibility into cryptographic assets. A lesson learned from past transitions is that you can’t change what you can’t see. Accordingly, the paper calls for developing an inventory – essentially a Cryptography Bill of Materials (CBOM) – cataloguing all cryptographic algorithms, libraries, keys, and protocols in use. This cryptographic inventory (akin to a software BOM but for crypto) is the foundation of agility planning. It lets organizations pinpoint where vulnerable algorithms (e.g. RSA or SHA-1) lurk in their stack and prioritize what to fix first. NIST’s strategic plan suggests “comprehensive visibility and an inventory of assets, such as code, libraries, applications, and associated cryptographic algorithms” as a first step. Industry experts have echoed this, with NIST recommending suppliers augment SBOMs with a Cryptography BOM for quantum readiness. In practice, building a CBOM means not just listing algorithms, but noting versions, locations, and dependencies – so you know, for example, which applications rely on OpenSSL 1.x with TLS 1.2 and RSA-2048, etc. Armed with this inventory, security teams can perform crypto risk assessments: identifying which systems are most sensitive or exposed and should get cryptographic updates first. This transforms crypto agility from an abstract ideal into a concrete, measurable program. In fact, NIST proposes using a “cryptographic policy-informed risk assessment engine” to continuously analyze the inventory, monitor cryptography in use, and recommend or automate mitigations according to policy and risk. It’s a shift toward data-driven governance of cryptography – something many CISOs will welcome.
Preparing for Failure – Agility in the PQC Era
A particularly striking aspect of CSWP 39 is its frank warning that even the new post-quantum cryptographic (PQC) algorithms are not guaranteed silver bullets. NIST underscores that the upcoming migration to quantum-resistant algorithms (e.g. Crystals-Kyber for encryption, Dilithium for signatures) is “certainly not the last transition required.” Future advances in cryptanalysis or computing could undermine these PQC schemes as well. In other words, we must not treat the 2020s PQC rollout as a one-and-done event. Crypto agility remains vital within the PQC era and beyond.
The white paper pointedly notes that the PQC transition is unprecedented in scope – replacing all public-key crypto – and that if it’s approached as a one-time retrofit, organizations risk baking in new rigidity. For example, PQC algorithms have much larger key sizes and signatures; if systems just “shoehorn” them in without agility, those size and performance constraints might be hard-coded, making the next change equally painful. NIST’s guidance encourages a more forward-looking approach: assume that some algorithms may fail or become suboptimal, and design now for graceful reconfiguration. Standards bodies are advised to maintain multiple mandatory-to-implement algorithms for protocols, precisely so there’s a plan B ready if the primary algorithm falters. In fact, the paper cautions that if a single mandatory algorithm is used to protect the negotiation (e.g. a hash or signature in a handshake), a flaw in it could be catastrophic – hence protocols might need “several mandatory-to-implement algorithms” of varying strengths to cover such scenarios.
The takeaway for architects and CISOs is clear: crypto agility is insurance against not only known threats but unknown ones. Even after deploying NIST’s PQC standards, organizations should continue to stay agile, monitor cryptanalytic news, and be ready to swap out a PQC algorithm if, say, a new mathematical attack emerges. Agility is an ongoing risk-management strategy, not a technical one-off fix.
Implications for IoT, Legacy Systems, and Supply Chain
Designing for agility is easier said than done, especially in constrained environments. NIST acknowledges the thorny challenges of embedded systems, IoT devices, legacy software, and hardware supply chains – areas where crypto is often hard-wired. In IoT and embedded devices, resources are limited and updates may be impractical. The paper notes that many real-time and embedded systems include only a minimal set of cryptographic primitives, fixed at compile-time to meet strict memory and timing constraints. Dynamic loading of new crypto modules “after deployment is often not supported” due to reliability and certification concerns. For such devices NIST advises a conservative strategy: implement the most future-proof algorithms available (e.g. larger key variants, hybrid modes) from the start, and plan for a shorter cryptographic lifetime of the device. In practice, this might mean choosing an algorithm suite that you expect to survive at least the device’s intended lifespan, and building in any upgradability that is feasible (some hardware, like FPGAs, can be field-updated to support new algorithms). It also means closely coordinating between cryptographers and product developers to forecast what “crypto shelf-life” a product needs.
For legacy systems that are critical but monolithic (e.g. an old banking system or SCADA controller where crypto is deeply embedded), NIST highlights the “crypto gateway” pattern as a stopgap. If you can’t easily modify the legacy application’s cryptography, place a modern cryptographic proxy in front of it – a bump-in-the-wire that performs encryption and authentication on the legacy system’s behalf. This encapsulation can extend the life of legacy systems by offloading crypto to agile external components, although it may introduce latency or complexity. The broader point is that organizations will need creative architectures to handle systems that aren’t agile: either isolate them behind gateways, segment them, or plan their retirement if they cannot be brought up to policy.
The supply chain dimension is significant as well. Crypto agility isn’t just an internal IT matter; it requires that vendors and integrators provide agile solutions, and that buyers demand them. The NIST paper positions technology supply chains as a critical part of the agility strategy – all components in the chain need to work in harmony during crypto updates. A “resilient technology supply chain” is one that enables modular crypto updates in products (e.g. your cloud provider, software vendor, or IoT device maker can ship you an algorithm upgrade without replacing the whole product). This has practical consequences: vendors of hardware and software are now on notice to build crypto-agility into new products, and customers (especially government) will increasingly require it in procurements. Indeed, industry guidance suggests that procuring organizations should start including contractual requirements for crypto agility and PQC support when buying new tech. We may soon see RFPs asking: Does your product have a cryptographic bill of materials? Can it accept new crypto algorithms via firmware update? If a vendor cannot demonstrate this, they risk being left out of lucrative contracts. Systems integrators, too, will need to prioritize agile components and architectures in the solutions they design, or face costly retrofits down the line.
Strategic Risk: Agile-Premium vs. Disposable-Static
One provocative issue for the future is a potential bifurcation in the market: an “agile-premium” class of products versus “disposable-static” ones. As crypto agility becomes a differentiator, we might see high-end IoT devices and software platforms advertising their updatable, modular cryptography – essentially selling peace of mind that the product won’t become obsolete overnight. These agile-premium products will likely command higher prices (and require ongoing support). On the other end, there could remain a swath of cheap, disposable IoT gadgets with hard-coded crypto that never gets updated – think of a $5 smart sensor that you simply have to throw away once its algorithms are deprecated. This dichotomy poses a strategic risk: if large portions of our infrastructure are built on “disposable-static” devices, the overall security ecosystem remains only as strong as its weakest links. Attackers will target the un-upgradable devices knowing they can’t be easily fixed. Organizations may have to decide which assets justify investment in agility and which do not – effectively segmenting their environment by risk tolerance. Over time, regulatory pressure might grow to phase out non-agile, non-updateable crypto in critical sectors, just as regulations today discourage use of unsupported software.
In practice, those near-zero agility assets become ticking time bombs that could force entire systems into emergency replacement. NIST’s guidance, by framing crypto agility as a risk management must-have, implicitly encourages decision-makers to avoid accumulating such technical debt.
Aligning with and Extending Prior Efforts
It’s worth noting that NIST CSWP 39 doesn’t emerge in a vacuum – it builds on years of industry and standards-body discussions about crypto-agility. Many security protocols (TLS, IPsec, etc.) have long included algorithm negotiation as a basic feature, and standards bodies like the IETF have promoted algorithm agility in protocol design. What’s different now is the breadth and urgency. Earlier efforts were often piecemeal or optional; NIST’s paper pulls them together into a comprehensive strategy and elevates their importance. It aligns with recent guidance like the NSA’s mandate that new National Security Systems acquisitions must be quantum-resistant by 2027 – but goes a step further in declaring that simply being quantum-resistant isn’t enough; you need the agility to keep adapting.
The paper also resonates with industry frameworks (for example, the FS-ISAC crypto-agility guidance for financial services) and complements Executive Order requirements for SBOM by essentially saying “and don’t forget the crypto in that BOM.” By formalizing a maturity model and calling for governance integration, NIST is pushing crypto-agility into the mainstream of cybersecurity management. This is a shift from seeing crypto choices as one-off technical decisions to seeing them as an ongoing, governable process – much like patch management or incident response.
Conclusion
For technical CISOs and security architects, NIST CSWP 39 should read like a call to action. It provides a policy blueprint to follow: treat cryptography as a living system that must be inventoried, monitored, and continually upgraded in alignment with your risk strategy. The paper’s tone is techno-strategic and clear-eyed – crypto agility is not framed as an academic ideal, but as a practical necessity for navigating the quantum era and beyond. As I wrote in “Rethinking Crypto-Agility,” true agility is less about effortless algorithm swaps and more about continuous, adaptive risk mitigation. NIST has now provided an official roadmap to achieve that.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.



