Forget Q-Day Predictions – Regulators, Insurers, Investors, Clients Are Your New Quantum Clock

Table of Contents
The Endless Q-Day Debate
For years, cybersecurity experts have debated “Q-Day” – the day when a cryptographically relevant quantum computer (CRQC) finally breaks modern encryption. Predictions range from alarmist claims that it’s imminent to skeptics arguing it’s so distant it may never happen.
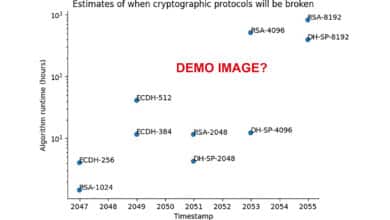
In reality, the truth lies between these extremes: quantum breakthroughs aren’t cracking RSA tomorrow, but recent advances suggest the fall of RSA-2048 encryption is plausible around 2030. I even made my own detailed Q-Day estimate, arguing that RSA-2048 could be broken by 2030. But don’t listen to me. To cut through the hype, I built Q-Day.org, a transparent, model-driven estimator (and related info) so anyone can stress-test assumptions and forecast the quantum risk for themselves.
Yet focusing on the exact Q-Day date misses the point. Every CISO must assume that powerful quantum computers will eventually arrive – and act accordingly now. Why? Because the ecosystem around you – regulators, clients, insurers, investors – started demanding it. Also, because even if Q-Day is a decade away, data being stolen today could be decrypted once quantum code-breaking becomes reality. This “harvest now, decrypt later” tactic means attackers might be stockpiling your encrypted data right now, planning to unlock it the moment a quantum “skeleton key” is available.
In short, the exact timing of Q-Day is increasingly irrelevant to your responsibilities. If you’re not preparing for the post-quantum era now, you’re falling behind.
Reason #1: Regulators Worldwide Impose 2030-2035 Deadlines
A flood of roadmaps, guidelines, and even laws has emerged from major economies, all pointing to a common horizon: roughly 2030-2035 as the timeframe to complete the transition to quantum-safe cryptography. Governments aren’t waiting for Q-Day to hit; they’re mandating proactive upgrades:
- United States: A 2022 law and White House directives have effectively set 2035 as the deadline for all federal systems to shift to post-quantum cryptography (PQC). The U.S. National Security Memorandum 10 (NSM-10) explicitly calls for completing the migration to quantum-resistant encryption by 2035. Federal agencies are already inventorying their cryptographic systems and planning transitions in line with an OMB strategy.
- Canada: Canadian authorities have echoed the U.S. timeline with a similar 2035 target for government systems, underscoring a North American consensus on urgency.
- European Union: The EU is moving even faster for critical infrastructure. In June 2025, the EU released a Coordinated PQC Transition Roadmap requiring high-risk sectors (like energy, finance, telecom) to complete post-quantum upgrades by end of 2030, with broader adoption by 2035. In other words, European critical infrastructure must be quantum-safe by 2030 – no excuses. By 2026, every member state must have a national PQC plan and pilot projects underway.
- United Kingdom: The UK’s National Cyber Security Centre (NCSC) has published similar guidance. Key milestones include defining a migration plan by 2028, tackling highest-priority systems by 2031, and completing a full PQC migration by 2035.
- Other Regions: Countries across Asia-Pacific and beyond are expected to announce comparable mandates. (As consultants working with governments, we at Applied Quantum know many new regulations are in the pipeline, some with even stricter enforcement.)
The message from regulators is crystal clear: Don’t wait. Organizations must begin crypto-agility efforts now, since a wholesale cryptographic overhaul can take years. In fact, NIST – after publishing its first batch of standardized quantum-resistant algorithms in 2024 – is actively urging companies to begin transitioning to the new standards as soon as possible. Early movers will find the process less disruptive and costly than laggards who procrastinate. If your systems protect sensitive or long-lived data, the 2030/2035 clock is ticking.
Reason #2: Customers and Vendors
It’s not just governments demanding action – your customers and business partners are starting to insist on quantum readiness. The most cyber-mature enterprises (think large banks, defense contractors, tech giants) have already begun pressuring their supply chain and vendors on this front. They recognize that security is only as strong as the weakest link in the chain. If you were a vendor, they want assurance you won’t become a quantum-era liability.
Concretely, many firms are adding PQC requirements into procurement policies and vendor contracts:
- Procurement Questionnaires: We’re seeing clients send detailed security questionnaires asking, “What is your quantum risk management plan? Are your products and services PQC-ready?”. Vendors without a good answer risk losing deals. Industry groups like FS-ISAC have even drafted sample questions to help companies assess each supplier’s post-quantum preparedness.
- Contract Clauses: Procurement departments are baking cryptographic agility into new contracts. They “vet vendors” and only buy from partners who are investing in PQC, and they lock in contract terms requiring vendors to upgrade crypto when needed. In practice, that means if you provide software or hardware, you may be contractually obligated to support NIST-approved quantum-safe algorithms by a certain date.
- Future-Proofing Standards: Customers now expect commitments that any products they buy today can be upgraded to PQC algorithms or operate in hybrid (classical + post-quantum) modes. RFPs increasingly include language on “crypto agility” – the ability to swap out cryptographic algorithms without massive re-engineering. In short, being quantum-ready is becoming a competitive differentiator. If you can’t demonstrate it, don’t be surprised when a client picks a rival that can.
Even if many companies are still in the early stages, the tide has turned. Forward-looking CISOs and procurement officers have started quietly raising the baseline for suppliers. The takeaway: prepare to answer these questions now – or risk being screened out of lucrative projects in the near future.
Reason #3: Insurance Industry
Another powerful driver you can’t afford to ignore is the cyber insurance industry. Insurers are in the business of pricing risk, and they’ve taken note of quantum computing’s disruptive potential. The last thing insurers want is to be on the hook for a massive breach that only happened because a client failed to upgrade their encryption in time. As a result, they are reassessing coverage and premiums in light of quantum threats (we know, we work with many of them):
- Coverage Carve-Outs: Some cyber insurance providers are quietly considering excluding quantum-related incidents from standard policies. This means if your data gets decrypted by a future quantum attack, your claim might be denied on the grounds that it was an “uninsurable” failure to maintain up-to-date security. We saw a similar pattern with insurers excluding acts of cyber war or nation-state attacks – now quantum vulnerabilities could be next on the exclusion list.
- Quantum Readiness as Underwriting Criteria: Don’t be surprised if renewal questionnaires start including items like “Have you begun migrating to post-quantum cryptography?” or “Do you have an inventory of quantum-vulnerable cryptosystems?” Companies that can answer “yes” (with evidence of real progress) will likely enjoy better terms. Those that haven’t started might face higher premiums or reduced coverage limits. In essence, insurers may reward quantum-ready organizations and penalize the laggards.
- Industry Warnings: Thought leaders in insurance are raising red flags. Reports from cybersecurity and insurance analysts (including Moody’s and specialist cyber insurers) highlight that quantum computing could render current encryption obsolete, leading to systemic risks. They urge insurers to update their models. An insurer might reason: if you choose to ignore a well-known upcoming threat, should they really pay out for the foreseeable fallout? It’s a tough but fair question.
From a CISO perspective, this translates to a boardroom concern. Insurance is often a last line of defense for cyber risk – if that safety net weakens due to quantum issues, the potential financial impact of a breach grows. Board directors and risk officers will expect the CISO to mitigate that by reducing the risk itself (i.e. upgrading cryptography), rather than hoping insurance will cover it. In fact, not preparing for quantum may even violate due care in the eyes of insurers and regulators, affecting everything from insurance claims to legal liability.
Reason #4: Investors and Boards
Finally, consider the message coming from investors, shareholders, and corporate boards. Over the past year, awareness of the quantum threat has exploded in executive circles. We’ve now seen shareholders and analysts directly ask companies about their quantum readiness during earnings calls. It’s a new variation of the tough questions boards have learned to ask about cybersecurity (e.g. “Are we protected against ransomware?”). Now they’re adding: “What’s our plan for the quantum computing threat?”
Some real-world examples illustrating this trend:
- Earnings Call Queries: In recent quarterly calls, CEOs and CFOs of large companies (especially in finance and critical infrastructure) have been put on the spot about quantum risks. Analysts are essentially probing, “How are you addressing the fact that quantum computers could undermine your security?” If you’re a CISO at a public company, you should be briefing your CEO with a good answer before that question comes up.
- Boardroom Briefings: More corporate boards are requesting deep-dive sessions on quantum cybersecurity. (I know, I’ve been called on to do that a dozen times already in September alone) They don’t want to learn the physics; they want to understand risk timing, business impact, and preparedness. As one director summed up: “How serious is the threat, how soon do we need to act, and what should we ask management to do about it?” Wise CISOs are proactively educating their boards on these points, highlighting that quantum cyber risk is ultimately business risk. When Q-Day hits, it’s not just an IT problem – it threatens every aspect of the enterprise from legal and compliance to reputation.
- Investor Expectations: Institutional investors (and even regulators like the SEC) are increasingly focused on cyber resilience as part of corporate governance. Quantum readiness is joining the list of metrics that signal a well-governed, forward-looking company. Just as companies are expected to have climate risk disclosures or pandemic contingency plans, a quantum risk mitigation plan is becoming part of due diligence. If two companies are otherwise equal, the one better prepared for post-quantum security might be seen as a safer long-term bet.
In short, ignoring the quantum issue could soon be seen as a governance lapse. No CISO wants to be in front of the board, explaining why they did nothing about a known ticking time bomb. And conversely, presenting a clear quantum transition roadmap can demonstrate leadership and foresight, which shareholders certainly appreciate.
Reason #5: Legal Liability Risk
There’s another clock you can’t ignore: the law. “Harvest now, decrypt later” means the breach has already begun – the data exfiltration is happening today – even if the pain (decryption) arrives years from now. That time‑lag doesn’t buy you leniency; it buys plaintiffs and regulators a better story. The question they’ll ask in 2032 isn’t “Did you guess Q‑Day correctly?” It’s: “What did a reasonable organization know in 2024–2025, and what did you do about it?”
Here’s how the liability might show up in practice (not a legal advice):
- Foreseeability is established. Governments, standards bodies, and the security community have been loud about quantum risk and HNDL. Once a risk is widely known and documented, “we didn’t think it was imminent” stops working. Courts and regulators judge you against what a prudent peer would have done given the facts available at the time.
- Negligence math won’t favor procrastinators. When leaders eventually apply the old B < P·L test to your choices, postponing crypto‑agility looks reckless: burden (B) is measured in program dollars and time; probability (P) is no longer zero; loss (L) for a mass decryption event is enormous. If you didn’t at least inventory crypto, map data shelf life, and plan a migration, you’ll have trouble explaining why.
- Regime‑agnostic accountability. In civil‑law environments, quantum readiness is increasingly treated as part of operational resilience and “state of the art” security—expect enforcement to precede headlines. In common‑law environments, enforcement and private lawsuits will follow the incident, but they’ll grade your past behavior. Different paths, same destination: a duty to act during the harvest phase.
- Contract and supply‑chain exposure. Many commercial agreements already promise “industry‑standard encryption,” crypto‑agility, or alignment with evolving standards. If your product or platform can’t be upgraded to post‑quantum algorithms in time, you could face breach‑of‑contract claims, indemnity fights, and lost deals—plus awkward disclosures to customers whose long‑lived data you promised to protect.
- Personal liability is trending up. Regulators and prosecutors have shown they’re willing to name individuals when security governance fails. CISOs and senior managers who never raised quantum risk, never sought budget, or certified compliance without a transition plan won’t have a great defense later. Documented diligence – boards briefed, risks logged, roadmaps funded – won’t just help the company; it protects you.
- Insurance won’t save you. As cyber insurers reprice quantum risk, exclusions and tougher underwriting will shrink the safety net. If you can’t evidence a credible transition path, expect worse terms – or no coverage – when you most need it.
Bottom line: legal risk runs on its own timeline, and it has already started. If regulators, customers, insurers, and investors are your new quantum clock, the law is the alarm bell. When two similar firms suffer quantum‑enabled data exposure in 2032, which one looks “reasonable” to a judge – the one that began crypto‑agility in 2025, or the one still debating timelines? For more information on this, see: “Post-Quantum Negligence: Legal Risks of Failing to Prepare for the Quantum Threat.”
Quantum Readiness Is Now a Business Mandate
Whether you personally believe Q-Day will come in 5 years or 50, the world around you isn’t taking chances – and neither can you. As a CISO, you’re now being implicitly (and sometimes explicitly) told by every corner of your ecosystem that quantum preparedness is mandatory. Regulators demand it via hard deadlines. Key clients and partners demand it in contracts and RFPs. Insurers will soon demand it as a condition of coverage. Investors and boards demand it as part of prudent risk management. Ultimately, the exact arrival date of a code-breaking quantum computer is not the central concern anymore.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.