All Post-Quantum, PQC Posts
-
Post-Quantum, PQC, Quantum Security
Marin’s Law on Crypto-Agility: Adaptability Determines Survivability
Thesis: Migration time to safer cryptography is inversely proportional to an organization’s crypto-agility. Formally: Let A denote an organization’s crypto-agility (0 ≤ A ≤ 1) and Y the wall-clock time required to replace a cryptographic primitive across all in-scope systems. Then Y ≈ K ⁄ A for some complexity constant K. As A → 0, Y → ∞. Corollary: Raising A today shortens all future…
Read More » -
Q-Day
How You, Too, Can Predict Q-Day (Without the Hype)
For three decades, Q-Day has been “just a few years away.” I want to show you how to make your own informed prediction on when Q-Day will arrive. Counting physical qubits by itself is misleading. To break RSA you need error‑corrected logical qubits, long and reliable operation depth, and enough throughput to finish within an attack‑relevant time window.
Read More » -
Post-Quantum, PQC, Quantum Security
CRQC Readiness Benchmark vs. Quantum Threat Tracker (QTT)
I will try and compare my proposed CRQC Readiness Benchmark with QTT, highlighting fundamental differences in methodology, assumptions, and philosophy, all in an effort to clarify how each approach informs our understanding of the looming “Q-Day.” The goal is to articulate why my benchmark and QTT produce different outlooks (2030s vs. 2050s for RSA-2048), and how both can be used together to guide post-quantum readiness.
Read More » -
Q-Day
The Trouble with Quantum Computing and Q-Day Predictions
The trouble with quantum computing predictions so far has been that too many have been more speculation than science, more influenced by bias than by balanced analysis. We have the tools and knowledge to do better. By embracing a data-driven, scenario-based approach, we can turn timeline forecasting from a source of confusion into a valuable planning aid.
Read More » -
Quantum Sovereignty
Quantum Tech and Espionage: What Every Researcher Must Know
To the untrained eye, espionage against scientists can be nearly invisible - it blends into everyday academic or business activity. But certain red flags and tactics surface again and again. Below is a consolidated list of common espionage methods (many from my own firsthand cases) used to target quantum tech researchers and organizations:
Read More » -
Post-Quantum, PQC, Quantum Security
Securing Quantum Readiness Budget Now
From a CISO and business leadership perspective, the ask is clear: we need to secure budget and resources now to begin the multi-year journey of quantum-proofing our organization. This includes funding for risk assessments, cryptographic inventory tools, new encryption software/hardware, staff training or hiring, and pilot projects to start integrating PQC. The investment is justified not only by the avoidance of a potentially catastrophic future…
Read More » -
Post-Quantum, PQC, Quantum Security
Risk-Driven Strategies for Quantum Readiness When Full Crypto Inventory Isn’t Feasible
Given the practical challenges, organizations may need to begin their quantum-readiness journey with a risk-driven approach rather than a theoretically perfect one. The essence of this strategy is to focus limited resources where they matter most – addressing the highest quantum-vulnerability risks first and implementing interim safeguards for the rest. Even the U.S. government’s guidance recognizes the need for prioritization. For example, the federal memo…
Read More » -
Leadership
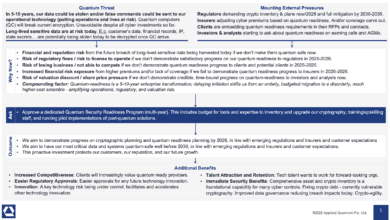
What is the Quantum Threat? A Guide for C‑Suite Executives and Boards
Boards do not need to dive into the scientific intricacies of qubits and algorithms, but they do need to recognize that this is a strategically important risk – one that can’t be simply delegated away. It requires the same level of governance attention as other enterprise-level risks like financial compliance, geopolitical factors, or pandemic preparedness. The comforting news is that if organizations act early, the…
Read More »