UK NCSC Releases “Timelines for migration to post-quantum cryptography”
London, UK (NCSC) – The UK’s National Cyber Security Centre (NCSC) this week unveiled new guidance on timelines for migrating to post-quantum cryptography (PQC), outlining a phased roadmap for organizations to shift their encryption methods to quantum-resistant standards by 2035. Announced just days ago, the guidance breaks down key milestones over the next decade to ensure a “smooth and controlled migration” that avoids the risks of a last-minute scramble or rushed implementations that might leave security gaps.
NCSC’s initiative comes amid growing global concern that emerging quantum computers could eventually crack today’s widely used encryption, putting sensitive data at risk. “Quantum computing is set to revolutionise technology, but it also poses significant risks to current encryption methods,” warned Ollie Whitehouse, NCSC’s Chief Technical Officer. The new timeline, he said, “provides a clear roadmap for organisations to safeguard their data against these future threats, helping to ensure that today’s confidential information remains secure in years to come”.
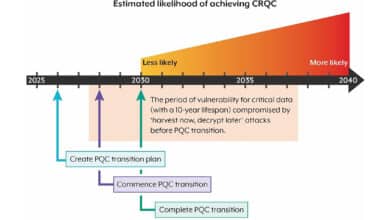
According to the NCSC, the roadmap defines three major phases for the PQC transition, with target dates in 2028, 2031, and 2035. These milestones are intended to guide technical decision-makers, large enterprises, critical infrastructure operators, and government agencies in planning their upgrades. Key timeline targets outlined in the guidance include :
By 2028: Assess and Plan. Identify all cryptographic assets and dependencies across the organization (a full discovery of where encryption is used), define the PQC migration goals, and build an initial migration plan. This discovery phase lays the groundwork for an orderly transition, ensuring no critical encrypted data or systems are overlooked.
By 2031: Prioritize and Upgrade. Execute the earliest and highest-priority quantum-resistant upgrades, focusing on critical systems and data that are most at risk. During this phase, organizations should also refine their roadmap – adjusting plans as PQC technologies mature – to achieve a comprehensive migration strategy for all systems.
By 2035: Complete the Transition. Finalize the migration to PQC across all systems, services, and products, thereby retiring or replacing legacy encryption that could be broken by quantum attacks. NCSC notes that a few specialized or legacy technologies might be challenging to convert by 2035, but “all organisations should work towards these key dates” as a general goal.
NCSC emphasizes that preparation must begin now so that migration steps can be performed methodically over multiple years and budget cycles. The guidance stresses that most steps involved – such as inventorying cryptographic systems, improving key management, and upgrading software – are core cybersecurity best practices in their own right. In fact, the agency suggests using the quantum transition as an opportunity to “build broader cyber resilience” into systems.
Notably, the NCSC assures smaller businesses that they won’t be left adrift. For many small and medium-sized enterprises (SMEs), the quantum-proofing of IT will occur via regular vendor updates – for example, web browsers, operating systems, and cloud services will gradually incorporate PQC in the coming years. Larger organizations and critical sectors, however, must take charge of their own crypto modernization plans, since they often operate custom systems or long-lived infrastructure that require significant planning and investment. By acting early, those major players can coordinate with suppliers and avoid falling behind. The overall message is one of urgency without panic: start planning and investing in PQC now, integrate it into normal tech refresh cycles, and thereby “reduce the risk of rushed implementations and security gaps” down the line.
Why the PQC Timeline Matters
The NCSC’s PQC migration timeline is more than just a technical guideline – it’s a strategic wake-up call for UK organizations. By publicly setting target dates (2028, 2031, 2035), the NCSC is signaling that the threat of quantum computing to current encryption isn’t science fiction, but a real risk with a probable time horizon.
Practically, this timeline helps organizations plan long-term investments in security. It offers CISOs and security leaders a concrete schedule to justify budget requests, workforce training, and system upgrades that will be needed to fend off “Q-Day” – the day a quantum computer can crack today’s cryptography.
Crucially, having milestones on the calendar means companies can integrate PQC migration into their multi-year digital transformation roadmaps now, rather than procrastinating until quantum attacks are imminent. The explicit dates (e.g. completing discovery by 2028) provide a common reference point for internal planning: enterprise risk committees and IT departments can work backward from these deadlines to ensure they meet them. This is especially important given that upgrading cryptography often touches many systems (from VPNs and databases to IoT devices), and some fixes may require waiting for vendor support or replacing legacy hardware.
The NCSC timeline effectively says: start early, because migrating encryption *“is a multi-year effort that will span more than one investment cycle and needs careful planning”. In other words, organizations that delay could find themselves scrambling later – or worse, managing significant legacy security risks if they miss the quantum-safe boat.
There’s also a cyber risk management angle. Threat actors might already be harvesting encrypted data today to decrypt in the future (“harvest now, decrypt later” attacks). The NCSC’s timeline underscores that to protect sensitive information with a long shelf life (think healthcare records, intellectual property, state secrets), organizations must upgrade to quantum-resistant encryption well before large-scale quantum computers arrive. By following the timeline and having PQC in place by the mid-2030s, UK organizations can ensure that even if adversaries obtain their data now, that data remains secure in the quantum era.
In short, NCSC’s guidance matters because it translates the abstract quantum threat into concrete action items and dates that business leaders can understand and rally around.