Getting Started With Quantum Readiness and PQC Migration
This page collects the PostQuantum.com articles you need to kick‑off and run a quantum‑readiness program, end‑to‑end. It’s organized along the lifecycle most teams follow: executive briefings & budget justification, cryptographic discovery/inventory, CBOM (Cryptographic Bill of Materials) creation, risk scoring & prioritization, road‑mapping and governance, pilots and migration patterns (hybrid/PQC/crypto‑agility), and operations (monitoring, vendor due diligence, training).
Notes & caveats. Real programs are messy: phases overlap and organizations differ. I’ve tagged each article to the dominant phase for clarity, but expect cross‑links. This is an opinionated, practitioner’s curation, not a standard, and it’s under development. No warranties; I aim to keep it current as guidance and tooling evolve. Feedback and corrections are welcome.
Start here: the blueprint (read first)
Quantum‑Readiness / PQC Full Program Description (Telecom Example) – This long-form case study walks through a realistic 10+‑year quantum‑readiness program for a large telecom, covering phases, workstreams, timelines, and order‑of‑magnitude cost and resource estimates. It’s effectively a reusable program blueprint you can adapt into your own charter, PMO plan, and RAID log, because it makes the scale, dependencies, and sequencing of PQC migration brutally concrete rather than abstract.
Phase 0 – Executive mandate & budget
Set the business case, deadlines, and secure funding.
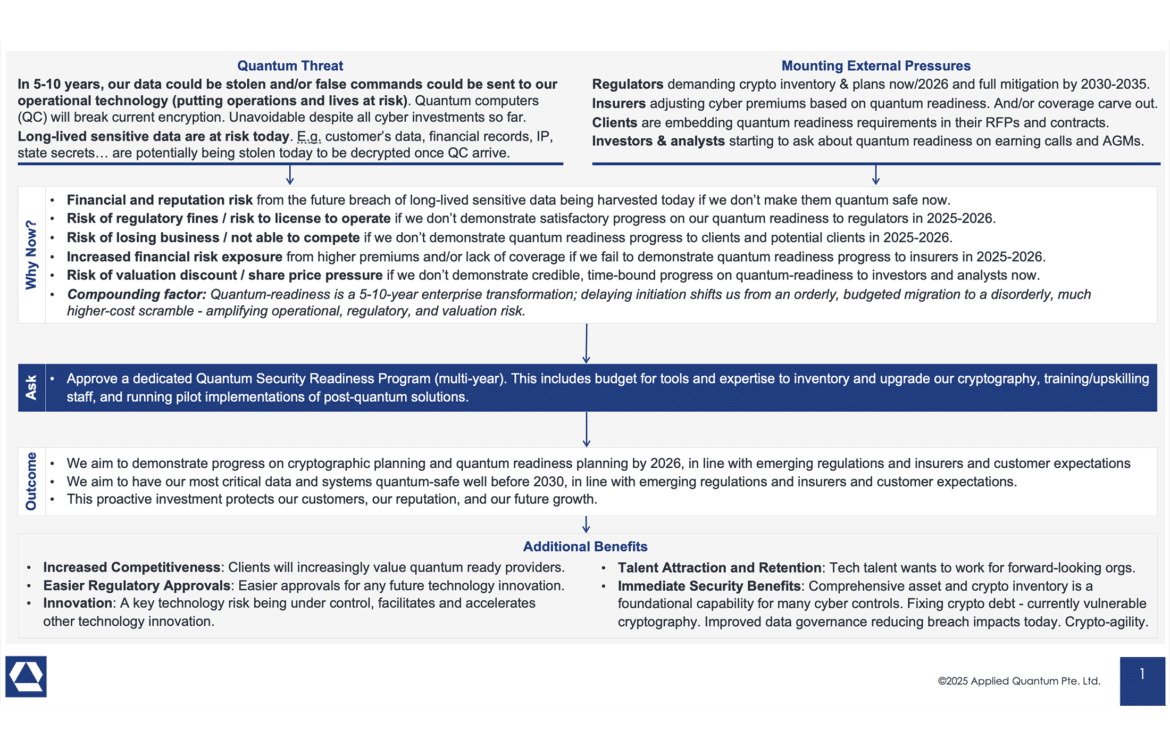
Forget Q‑Day Predictions – Regulators, Insurers, Investors, Clients Are Your New Quantum Clock – This piece reframes urgency away from speculative “Q‑Day” dates and toward hard external pressures: 2030–2035 regulatory deadlines, procurement and contract requirements, insurer underwriting criteria, and investor/board expectations. It arms CISOs with a business-centric narrative for “why now?” that does not depend on betting on a specific quantum timeline, making it ideal for board decks and funding papers that need a clear, defensible clock.
Securing Quantum Readiness Budget Now – Here we build a structured business case for quantum readiness by tying together quantum risk (especially harvest‑now‑decrypt‑later), regulatory pressure, client/vendor expectations, cyber‑insurance trends, and competitive advantage from acting early. The article lays out concrete “benefit buckets” such as improved asset and crypto inventory, cleanup of crypto‑debt, better vendor security, and stronger data governance, giving you a template for a CISO budget deck rather than just abstract risk talk.
How CISOs Can Use Quantum Readiness to Secure Bigger Budgets (and Fix Today’s Problems) – This one positions quantum readiness as a lever to fund long‑overdue work: asset discovery, cryptographic visibility, remediation of weak configurations, supply‑chain hardening, and data hygiene. It’s a playbook for turning PQC migration into an umbrella program that addresses today’s security gaps while preparing for tomorrow, helping you argue that this isn’t “science‑fiction spend” but a way to modernize the estate using a new compliance and risk mandate.
Ready for Quantum: Practical Steps for Cybersecurity Teams – This long-form guide is a bridge between “why this matters” and “what the security team actually does.” It lays out business drivers (data longevity, infrastructure lifetime, regulation, insurance, competitive positioning) and then walks through do’s/don’ts, team structure, awareness campaigns, inventories, risk assessments, and early third‑party engagement – essentially a proto‑program charter from a CISO’s point of view. It’s a natural “starter playbook” for security leaders who just got budget approval and now need to turn that mandate into concrete workstreams and governance.
What is the Quantum Threat? A Guide for C‑Suite Executives and Boards – This is your plain‑English board primer: it explains the quantum threat, harvest‑now‑decrypt‑later, and Q‑Day without physics, and frames the issue as a governance and fiduciary risk rather than an IT curiosity. It ends with specific questions directors should be asking management, so you can use it as a pre‑read or appendix in board materials to bring directors to a common baseline before you ask for money and mandate.
Harvest Now, Decrypt Later (HNDL) Risk – This article is your deep dive on the “steal today, decrypt tomorrow” problem: it explains how adversaries can record encrypted traffic or exfiltrate encrypted stores now and wait for cryptographically relevant quantum computers to arrive, focusing on long‑lived secrets (state data, health records, trade secrets) and why forward secrecy is no longer enough. It then outlines practical countermeasures: identify long‑life data, harden against data theft, adopt crypto‑agility, watch the “quantum gap,” and train teams – giving CISOs concrete arguments and action points when they explain why migration must start years ahead of Q‑Day.
Trust Now, Forge Later (TNFL) – The Overlooked Quantum Threat – Where HNDL is about future loss of confidentiality, this piece zooms in on the integrity side: quantum‑enabled forging of digital signatures and certificates that underpin software updates, device identity, PKI, safety‑critical OT commands, and financial transactions. It argues that TNFL could be even more dangerous than HNDL, because once signatures can be forged at scale, you get “instant and invisible” compromises, including cyber‑kinetic scenarios (malicious firmware in industrial or grid systems) that look like normal, trusted operations. This is ideal material to brief boards and risk committees that integrity and safety are at least as important as privacy in the quantum story.
Q‑Day Isn’t an Outage – It’s a Confidence Crisis – This article reframes Q‑Day not as a Hollywood “everything breaks at midnight” outage, but as an overnight collapse of trust once the first credible RSA/ECC break is demonstrated. It explains that while early quantum attacks will be expensive and focused on crown‑jewel targets, the perception that our crypto is broken will drive panic: bank runs, sudden flight to “quantum‑safe” brands, emergency audits, regulatory pressure, and frantic repricing of digital risk across finance, government, critical infrastructure, and comms. It’s the perfect narrative to show executives that quantum readiness is about preserving confidence in digital systems, not just avoiding a technical incident.
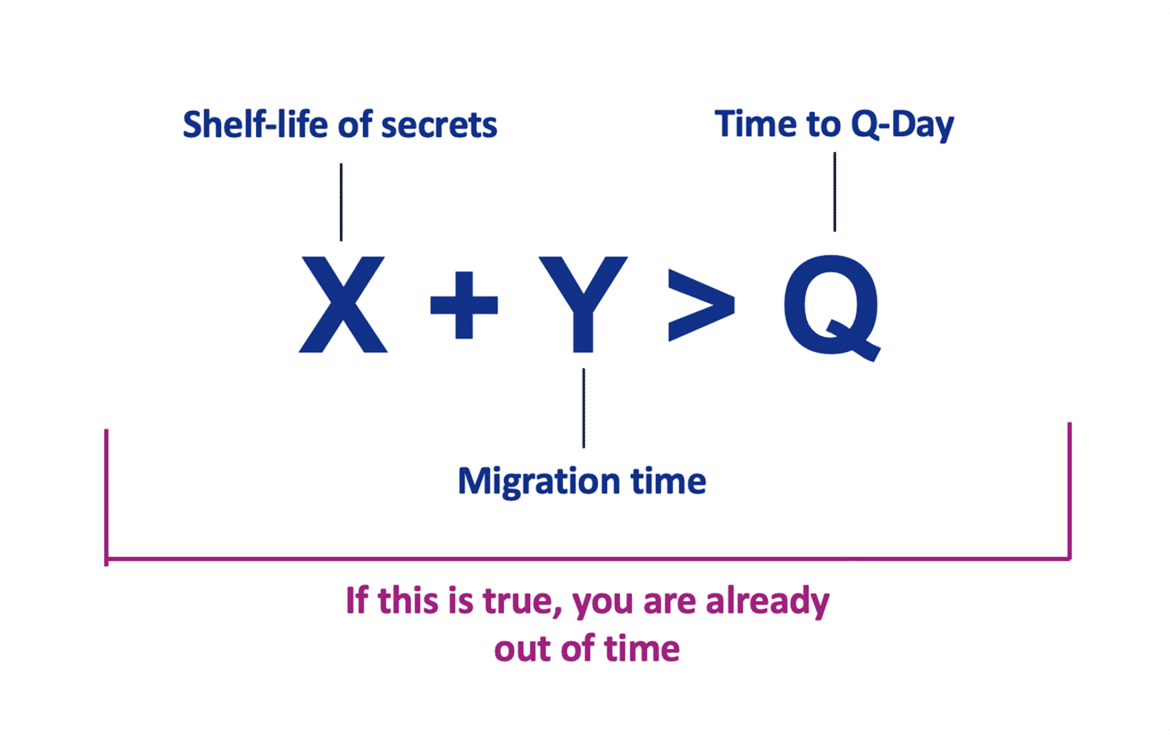
Mosca’s Theorem and Post‑Quantum Readiness: A Guide for CISOs – This is your cleanest explanation of Mosca’s inequality (X + Y > Q): how the lifetime of sensitive data (X), the time needed to migrate (Y), and the time until quantum code‑breaking (Q) interact to determine whether you’re already late. It provides a simple risk‑math frame CISOs can use with boards: if your data must remain confidential longer than the remaining quantum timeline minus your migration time, then you’ve already run out of runway. This helps turn abstract “someday quantum risk” into a defensible, quantified schedule for starting inventories, CBOM, and PQC pilots now.
The Skill Stack a CISO Needs for Crypto‑Agility and Quantum Readiness – Instead of hunting unicorn “quantum experts,” this guide decomposes quantum‑readiness into skill domains you mostly already have: governance, cryptographic discovery and CBOM, PKI/KMS/HSM engineering, protocol and app engineering, testing and performance, data governance/compliance, and vendor management. For each domain it spells out required skills, why they matter, candidate existing roles, upskilling paths, and performance indicators, making it a practical tool for designing your operating model, assigning ownership, and planning training for the program.
Post‑Quantum Negligence: Legal Risks of Failing to Prepare for the Quantum Threat – This long essay recasts quantum risk as a negligence and fiduciary‑duty issue, not just a technical choice. It analyzes HNDL and TNFL through legal lenses like foreseeability and the Learned Hand test, surveys emerging EU/UK/US regulatory signals, and walks through who could be on the hook when quantum‑enabled breaches occur: the company, individual directors, vendors, and even advisors. It’s especially useful when boards or general counsel ask, “What happens if we don’t act?” – you can point them to this piece as a structured scenario analysis of how regulators, courts, and plaintiffs might treat failure to prepare as unreasonable in light of today’s public guidance.
Phase 1 – Discovery & inventory (assets + crypto)
Get visibility fast; combine top‑down scoping with bottom‑up technical discovery.
How to Perform a Comprehensive Quantum Readiness Cryptographic Inventory – This is the “how‑to manual” for cryptographic inventory: it explains why inventory is foundational, unpacks the real‑world obstacles, and then walks through discovery techniques across code, runtime, networks, configurations, cloud, hardware/firmware, and certificates. It also sketches a project plan and shows how inventory results feed into a CBOM, giving you something very close to a delivery playbook you can hand to an internal team or vendor when kicking off discovery.
Cryptographic Inventory Vendors and Methodologies – Here we catalog the landscape of crypto‑inventory tools – IBM, Keyfactor/InfoSec Global, SandboxAQ, CryptoNext, Quantum Xchange, PQStation, QryptoCyber, ISARA, Tychon, AppViewX, and open‑source options – describing each vendor’s approach, strengths, blind spots, and ideal use cases. It’s the piece you use when deciding which mix of static, runtime, passive, and agent‑based tools to bring into a pilot or RFP, and when explaining to procurement and leadership why no single product will give you full coverage.
Dos & Don’ts of Crypto Inventories for Quantum Readiness – This article is essentially a pattern/anti‑pattern guide: it shows why interview‑driven, spreadsheet‑only inventories fail, highlights common traps (like asking asset owners to “list all crypto”), and lays out best practices for scoping, automation, and centralizing results. It’s particularly useful for setting realistic expectations with executives and project managers so they understand why you need tooling, why this isn’t a one‑off survey, and what “good enough” looks like for early phases.
Risk‑Driven Strategies for Quantum Readiness When Full Crypto Inventory Isn’t Feasible – Recognizing that a perfect inventory may be unattainable, this piece advocates a risk‑driven approach: prioritize systems that handle high‑value or long‑lived data, critical services, externally exposed interfaces, and highly connected nodes. It gives you a pragmatic triage strategy combining partial discovery with compensating controls, helping you start quickly, focus effort where it matters most, and stay aligned with regulatory guidance even when you can’t “find everything.”
The Challenge of IT and OT Asset Discovery – This article zooms out from cryptography to the underlying asset problem, explaining why modern IT and OT environments make even basic asset discovery extraordinarily hard – shadow IT, legacy equipment, dynamic cloud, industrial controllers, and IoT. It’s a good primer for senior leaders and risk committees on why cryptographic inventory is inherently difficult, and why investing in better asset visibility is a prerequisite for any serious quantum‑readiness program.
Upgrading OT Systems to Post‑Quantum Cryptography (PQC): Challenges and Strategies – This OT‑focused piece looks at long‑lived industrial systems, vendor‑locked protocols, safety and regulatory constraints, and strict maintenance windows, and then lays out practical tactics: crypto‑gateways, overlay encryption, segmentation, compensating controls, and vendor engagement. Use it to brief OT leaders and plant managers on what PQC migration means for them and to design realistic OT pilots that don’t break safety cases or uptime SLAs.
Quantum Era Demands Changes to ALL Enterprise Systems – Here we challenge the “just swap RSA for Kyber” myth by showing that PQC touches identity, data storage, application architectures, networks, cloud, OT, IoT, and even AI and analytics stacks. It’s excellent material for early stakeholder education: helping application owners, data teams, identity architects, and business leaders understand that quantum readiness is a whole‑of‑enterprise program, not a point upgrade handled by the PKI team in isolation.
Phase 2 – CBOM & documentation
Create durable, queryable documentation of cryptography and sensitive data.
Cryptographic Bill of Materials (CBOM) Deep‑Dive – This deep dive defines what a CBOM is, how it differs from and complements SBOM, and what fields you actually need – algorithms, key sizes, protocols, libraries, certificates, key lifetimes, usage contexts, and associated systems. It also links CBOMs to CycloneDX and other standards, and explains how to generate and maintain them from your inventory tooling and CI/CD pipelines, making it a blueprint for building the durable cryptographic documentation layer your program will depend on.
Bills of Materials for Quantum Readiness: SBOM, CBOM, and Beyond – This article generalizes the concept to a holistic “BOM fabric”: SBOM for software components, CBOM for cryptography, DataBOM for sensitive data, and HBOM for hardware. It shows how those artifacts interlock to support PQC migration, vulnerability management, and supply‑chain governance, giving you the conceptual framework to argue for coordinated BOM initiatives instead of yet another siloed spreadsheet.
Phase 3 – Risk scoring & prioritization
Translate visibility into a defensible, sequenced plan.
Quantum Readiness Assessment – This piece defines what a Quantum Readiness Assessment actually is: an in‑depth review that looks at cryptographic usage, governance, inventories, vendor and supply‑chain dependencies, data at risk, crypto‑agility, and regulatory exposure. It explains how to structure the assessment, what outputs (e.g. scores, heatmaps, prioritized remediation lists) you should expect, and how those feed into roadmap, governance, and audit readiness – so you can either design your own QRA or be an educated buyer of external assessments.
Phase 4 – Roadmap & governance
Stand up program mechanics and a realistic glidepath.
Planning the First Year of a Quantum Readiness Program – This article turns the big multi‑year vision into a concrete 12‑month plan, roughly quarter‑by‑quarter: securing mandate, setting scope, starting discovery, launching pilot inventories, standing up governance, and initiating early PKI/HSM work. It’s ideal for a CISO or program manager who needs “what do we actually do this year?” and wants a realistic starter roadmap and set of milestones tied to Phases 0–4.
Quantum Readiness / PQC Migration Is The Largest, Most Complex IT/OT Overhaul Ever – So Why Wait? – This is a positioning piece you can send to skeptical executives: it argues that PQC migration will be larger and more complex than Y2K, but also that delaying only makes it more expensive and risky. It’s written to reset expectations – no one‑click patch, lots of OT/IoT/network complexity – and to push stakeholders toward early action while the window for orderly migration is still open.
Phase 5 – Pilots & migration patterns (hybrid/PQC/crypto‑agility)
Prove feasibility, then scale with crypto‑agility.
Hybrid Cryptography for the Post‑Quantum Era – This article explains hybrid schemes that combine classical and post‑quantum algorithms – for example, doing both an elliptic‑curve and a Kyber key exchange or dual classical + PQ signatures – and walks through how this looks in protocols like TLS, SSH, and IPsec. It helps you design realistic early pilots that are standards‑aligned and interoperable, and gives you clear talking points when explaining to architects and risk officers why hybrid is a sensible bridge strategy.
Introduction to Crypto‑Agility – Here we introduce crypto‑agility as the ability to change algorithms, keys, and protocols quickly without redesigning entire systems, and we tie it explicitly to post‑quantum migration and future algorithm changes. It outlines principles such as abstraction of crypto, decoupled libraries, policy‑driven configuration, and strong inventories, giving you a conceptual anchor for all the architecture, process, and tooling work that sits alongside pure PQC deployment.
Marin’s Law on Crypto‑Agility: Adaptability Determines Survivability – This is a deliberately simple law: time to migrate (Y) is inversely proportional to crypto‑agility (A), so as agility approaches zero, migration time tends toward infinity. The article uses that relationship to propose practical indicators and OKRs – things like percentage of systems using configurable crypto modules or prevalence of CBOM coverage – helping you quantify and communicate why improving agility is as important as picking the “right” PQC algorithms.
Rethinking Crypto‑Agility – Here we critique the unrealistic vision of “one‑click algorithm swap,” reframing crypto‑agility as an operational capability that looks more like vulnerability management or incident response: continuous detection of weak crypto, rapid decision on mitigations, and a toolbox of techniques such as hybrid encryption, overlays, and segmentation. It’s the article you use to reset expectations with architects and executives about what near‑term crypto‑agility can and should be, and to define a more achievable target state for your program.
PQC Is Necessary, But Not Sufficient – Building Quantum Resilience the Right Way – This article argues that “just deploy NIST PQC” is not a realistic security strategy: it walks through the state of PQC standards, implementation pitfalls (KyberSlash‑style side channels, timing and fault attacks), the risk of future algorithmic surprises, and the need for crypto‑agility even in a PQC world. It then lays out a “PQC+” blueprint: governance and agility, hybrid key exchange and signatures, hardened implementations, modernized PKI/protocols, layered and data‑centric security, and zero‑trust‑aligned architecture – including a pragmatic 90‑day starter plan. It’s an excellent bridge from conceptual crypto‑agility pieces into concrete design principles for pilots and scalable rollout patterns.
Mitigating Quantum Threats Beyond PQC – This piece surveys complementary strategies beyond simply deploying NIST PQC algorithms – things like minimizing secret exposure, tokenization, isolation and segmentation, application‑layer protections, and where quantum key distribution might make sense. It’s useful when you’re building a defense‑in‑depth roadmap and want to show that “doing PQC” is necessary but not sufficient, especially for systems that can’t be upgraded easily or that must assume long‑term adversary capabilities.
Evaluating Tokenization in the Context of Quantum Readiness – Here we argue that tokenization is a powerful but underused lever for quantum readiness: by replacing long‑lived sensitive data (e.g. PANs, IDs, health records) with tokens, you reduce the scope of PQC migration and the blast radius of future cryptographic failures. The article walks through tokenization patterns, trade‑offs, and governance considerations, helping risk and data teams factor tokenization into their PQC strategy rather than treating it as a separate compliance tool.
Phase 6 – Infrastructure & performance
Modernize PKI/HSM, harden networks, and test end‑to‑end impacts.
Common Failures in a Quantum Readiness Program – This short piece is basically the “anti‑pattern checklist” for PQC deployments: treating PQC as a simple library swap, ignoring handshake bloat and middlebox behavior, assuming HSMs/KMSs “just support PQC,” and running with shallow crypto inventories. It provides crisp examples (e.g., PQ signatures that don’t fit existing cert formats, TLS ClientHello fragmentation breaking middleboxes, misleading HSM firmware marketing) and suggests specific mitigations like end‑to‑end testing, handshake size measurement, and early vendor POCs. It’s a great pre‑read for network, PKI, and platform teams before they dive into your more detailed infrastructure articles in this phase.
Infrastructure Challenges of “Dropping In” Post‑Quantum Cryptography (PQC) – This article attacks the “drop‑in replacement” myth by examining how PQC algorithms (like ML‑KEM/Kyber and Dilithium) stress real infrastructure: larger handshakes, longer certificate chains, higher CPU and memory usage, and brittle middleboxes that may choke on bigger keys or messages. It’s the piece you give to network, platform, and PKI teams to justify lab testing, capacity planning, and staged rollouts instead of blindly switching algorithms in production.
Post‑Quantum Cryptography (PQC) and Network Connectivity: Challenges and Impacts – Here we go network‑type by network‑type – WAN, mobile, LPWAN, satellite, constrained IoT – and analyze how PQC affects latency, bandwidth, reliability, and device constraints. It provides concrete examples of where PQC might break existing assumptions (e.g. on low‑bandwidth links) and offers mitigation ideas, making it a practical guide for network architects and system designers who need to understand the connectivity consequences of their PQC choices.
Challenges of Upgrading to Post‑Quantum Cryptography (PQC) – This earlier (2019) article gives a concise, business‑friendly overview of the upgrade problem: universal exposure across devices, the often‑ignored non‑IT and OT environments, performance and efficiency costs from larger keys, audit and maturity questions around new algorithms, supply‑chain and vendor coordination, and the sheer cost and organizational lift of the transition. It pairs well with the newer, more detailed “PQC Challenges” article by providing a “big picture” narrative you can still hand to executives or program sponsors who don’t want a 9‑minute deep dive but need to grasp why this is bigger than Y2K and fundamentally not a patch‑Tuesday exercise.
Post‑Quantum Cryptography PQC Challenges – This is a broad overview that pulls together the main headwinds: standards still evolving, performance and footprint issues, implementation pitfalls, vendor and supply‑chain readiness, governance and talent gaps, and cost. It functions well as an executive summary for senior stakeholders who need a single article that captures why migration is necessary, difficult, and long‑term – useful for steering committees and risk forums.
Phase 7 – Vendor & supply chain
Make third parties part of your plan, not a blocker.
Quantum Readiness Is Not (Just) a Vendor Problem – This piece tackles the very common attitude of “our cloud/infra/application vendors will sort this out for us,” using survey data and regulatory trends to show why that’s a dangerous misconception. It underlines that boards and CISOs remain accountable; highlights the need for organization‑wide crypto inventory across internal and vendor‑supplied components; and outlines how to engage third parties constructively (RFP questions, roadmap expectations, hybrid support, governance) without outsourcing responsibility. It’s a good framing article before the more operational “Engaging and Managing Vendors…” post, emphasizing that vendor management is one workstream within a much larger enterprise program, not the program itself.
Engaging and Managing Vendors for Quantum Readiness – This article is your vendor playbook: it suggests question sets for security questionnaires, RFP and contract clauses about PQC support and crypto‑agility, and ways to align supplier roadmaps with your own timelines. It also stresses early engagement and ongoing cadence, warning that vendors who lag on PQC can become blockers for your program – making this essential reading for procurement, vendor management, and any CISO trying to shift the vendor conversation from “we’ll patch later” to “show us your quantum plan now.”
Appendix – Sector & system deep‑dives (great for stakeholder education)
Use these to explain complexity to non‑crypto stakeholders.
Telecom’s Quantum‑Safe Imperative: Challenges in Adopting Post‑Quantum Cryptography – This telecom‑specific deep dive covers PQC challenges across 5G/6G core and IMS, lawful intercept, roaming, distributed edge, vendor dependencies, and standards coordination, grounded in real program experience. It’s a powerful briefing for telecom executives and regulators, and also a useful analog for other critical‑infrastructure sectors trying to grasp what PQC migration looks like in a highly interconnected, regulated, and vendor‑constrained environment.
Cryptography in a Modern 5G Call: A Step‑by‑Step Breakdown – Here we follow a single 5G voice call with roaming and enumerate the cryptography at each step: SIM authentication, radio encryption, core signaling, roaming interfaces, IMS call setup, and backend billing. It’s a great educational tool for showing non‑crypto stakeholders just how many cryptographic layers exist in a seemingly simple transaction – and therefore why inventories, CBOMs, and careful migration planning are unavoidable in telecom and similar complex systems.
Cryptographic Stack in Modern Interbank Payment Systems – This article does the same for cross‑border payments: from customer‑to‑bank channels, internal bank systems and HSMs, SWIFT messaging, correspondent banking, and central‑bank settlement, down to API security and software update mechanisms. It’s especially useful for financial‑sector stakeholders, showing them how deeply cryptography underpins their rails and why PQC migration will require coordination across multiple institutions and regulators, not just an internal code change.