ACSC’s Post-Quantum Plan: Start Now, Plan for Longer Execution
22 Sep 2025 – The Australian Cyber Security Centre (ACSC) – via the Australian Signals Directorate (ASD) – has published updated guidance titled “Planning for Post-Quantum Cryptography.” This publication underscores the looming threat that cryptographically relevant quantum computers (CRQCs) will pose to current encryption.
ACSC warns that once quantum machines mature, they could break today’s public-key algorithms (like RSA and ECC), endangering the confidentiality and integrity of sensitive data. In response, the guidance urges organizations to start preparing now for a transition to post-quantum cryptography (PQC) – new cryptographic algorithms designed to resist quantum attacks. Early action is crucial, ACSC notes, because “deploying protections against a CRQC may take longer than expected” and the timeline for a usable quantum computer is uncertain. Additionally, adversaries might “harvest now, decrypt later,” stockpiling encrypted data today to decrypt once quantum capabilities arrive.
Encouragingly, ACSC joins other national security agencies in sounding the alarm about the quantum threat. Around the world, there is a growing consensus that organizations must begin quantum readiness efforts now. For example, a recent industry survey found an overwhelming majority of organizations have not even started drafting a PQC roadmap, even though experts agree the migration process is complex and lengthy.
In the U.S., the National Institute of Standards and Technology (NIST) has already standardized several PQC algorithms (with more on the way by 2026), and government mandates are emerging to drive adoption in federal agencies. The U.K.’s National Cyber Security Centre (NCSC) similarly advises that planning for PQC migrations should commence immediately, emphasizing that crypto-agility and careful preparation are key.
It’s heartening to see ACSC add its voice to this global chorus. By raising awareness and providing guidance, ASD/ACSC is helping enterprises treat the quantum threat with the seriousness it deserves. In particular, the Australian guidance recommends organizations cease using traditional asymmetric cryptography by 2030, replacing it with ASD-approved post-quantum algorithms. This clear deadline sends a strong signal: don’t wait until a quantum breaker arrives; begin the transition early so that your data and systems remain secure.
An Aggressive Two-Year Transition Timeline
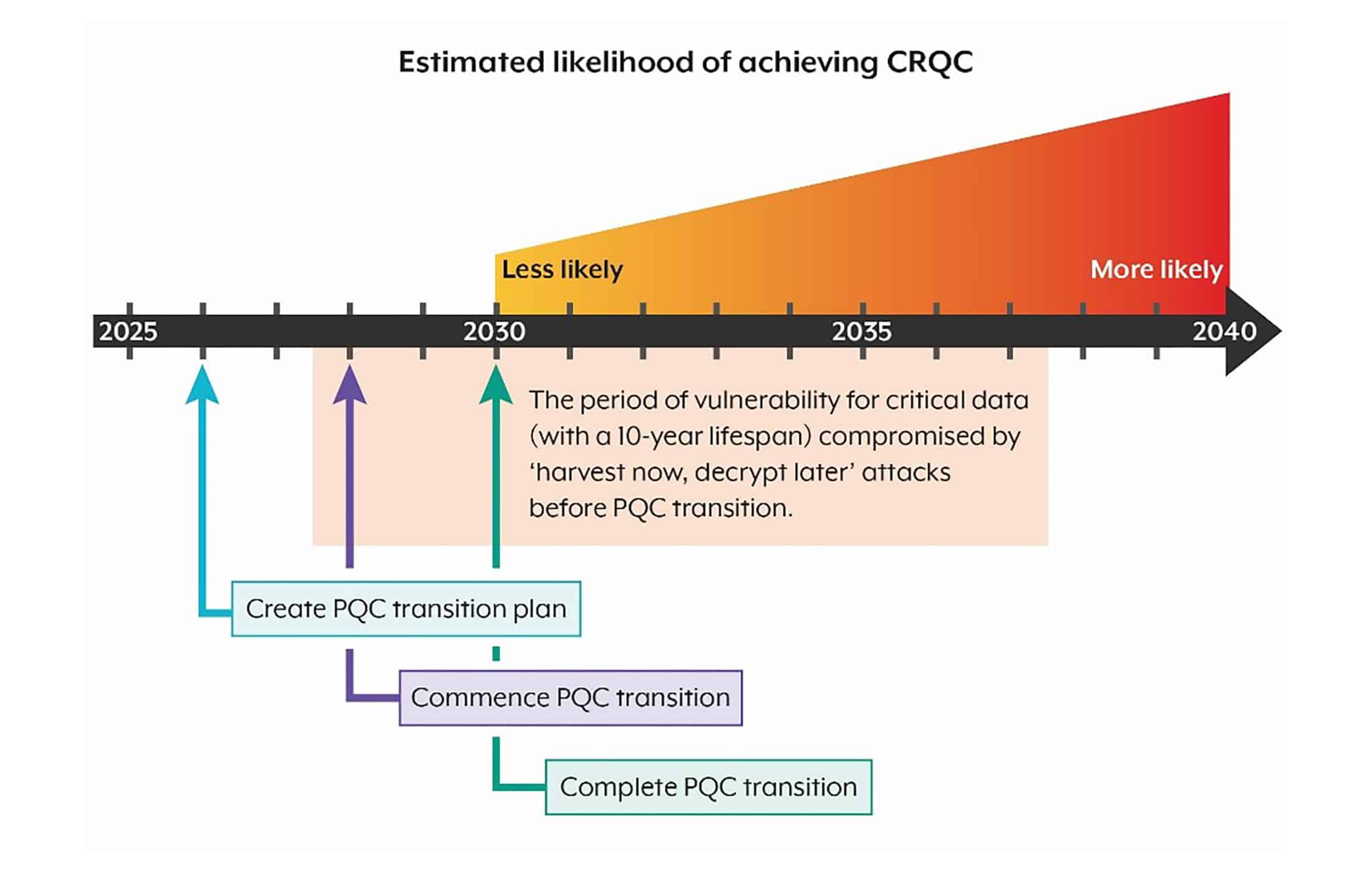
ASD’s recommended PQC transition timeline (in blue/purple/green) plotted against the rising likelihood of a powerful quantum computer by year. The goal is to finish migrating to post-quantum cryptography by 2030, before quantum attacks become a serious risk.
While ACSC’s push to “start planning for PQC right away” is wise their recommended timeline raises some concerns. The guidance outlines specific transition milestones: by end of 2026 organizations should have a detailed PQC transition plan; by end of 2028 they should have begun implementing PQC (starting with their most critical and high-risk systems); and by end of 2030 the transition should be completed across the organization. In other words, ASD envisions that once an enterprise kicks off its migration (by 2028), it can fully replace or upgrade its cryptography within about two years. For small or greenfield environments, a two-year execution phase might be achievable. For most large enterprises, however, a 2-year window to entirely swap out entrenched cryptographic systems is overly optimistic.
The reality is that migrating to post-quantum cryptography is a massive, multi-year undertaking for typical large organizations. A recent roadmap from the Post-Quantum Cryptography Coalition (which includes MITRE, Microsoft, and IBM) emphasized that transitioning to PQC “is a complex process” likely to take enterprises multiple years to complete, requiring meticulous planning and execution. This isn’t a simple drop-in replacement; it involves discovering everywhere current cryptography is used (often in thousands of applications and devices), updating or replacing hardware and software components, ensuring interoperability, and testing extensively to avoid breaking systems. In many cases, vendors must provide updates or new products, and legacy or IoT devices (think ATMs, industrial controllers, satellites, etc.) may not be easy to upgrade at all. These challenges mean that a full transition will stretch over much of the decade, not just a two-year sprint.
Indeed, analysts predict a lengthy timeline. Research by Moody’s Investors Service, for instance, concluded that implementing post-quantum cryptography across all affected devices “will be long and costly,” potentially on the order of 10 to 15 years due to operational hurdles. U.S. officials have similarly estimated that widespread adoption of new quantum-resistant cryptographic standards could take well over a decade. Such projections dwarf the ACSC’s diagram that suggests wrapping up the transition by 2030. Large enterprises – especially those with complex, global IT estates – typically need significant time to inventory their cryptographic usage, remediate or replace systems, and manage the risks of such a profound change. It’s telling that the Moody’s report likened the PQC migration to the Y2K remediation effort in scope. Like Y2K, this transition will require concerted effort and investment over years to retrofit and secure countless systems.
To be fair, the ACSC guidance acknowledges that its 2030 target includes contingencies and that organizations should account for internal delays or obstacles. The intent is likely to set a bold but clear goal to galvanize action, rather than a hard-and-fast rule for every situation. For many organizations, 2030 may serve as an aspirational deadline to motivate progress. However, treating 2030 as a one-size-fits-all “finish line” could be risky. Enterprises that discover they cannot replace all cryptographic components in time should not despair or give up – instead, they should prioritize wisely (as ACSC advises) and tackle the most sensitive or hard-to-fix areas first. Critical data with long-term confidentiality needs and systems that will take the longest to upgrade (due to their complexity or vendor dependencies) should be at the front of the queue. Less critical or easily upgradable systems can follow. This phased approach ensures that even if the full transition extends beyond 2030, the highest risks are addressed early, and the organization’s most valuable assets remain protected.
In summary, Australia’s ACSC deserves credit for elevating post-quantum cryptography on the national agenda and providing practical guidance to get started. Their message aligns with global expert opinion: don’t wait for the quantum threat to become imminent; begin your preparations now. At the same time, it’s important to approach the timeline with realism. Two years is unlikely to be sufficient for large enterprises to complete a PQC overhaul, so leaders should plan for a longer journey. By setting interim goals (like ACSC’s 2026 and 2028 milestones) and securing executive support, organizations can make steady progress toward quantum resilience. The key is to start the transition early, plan thoroughly, and be prepared to adapt as technology and threats evolve.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.