Securing Quantum Readiness Budget Now
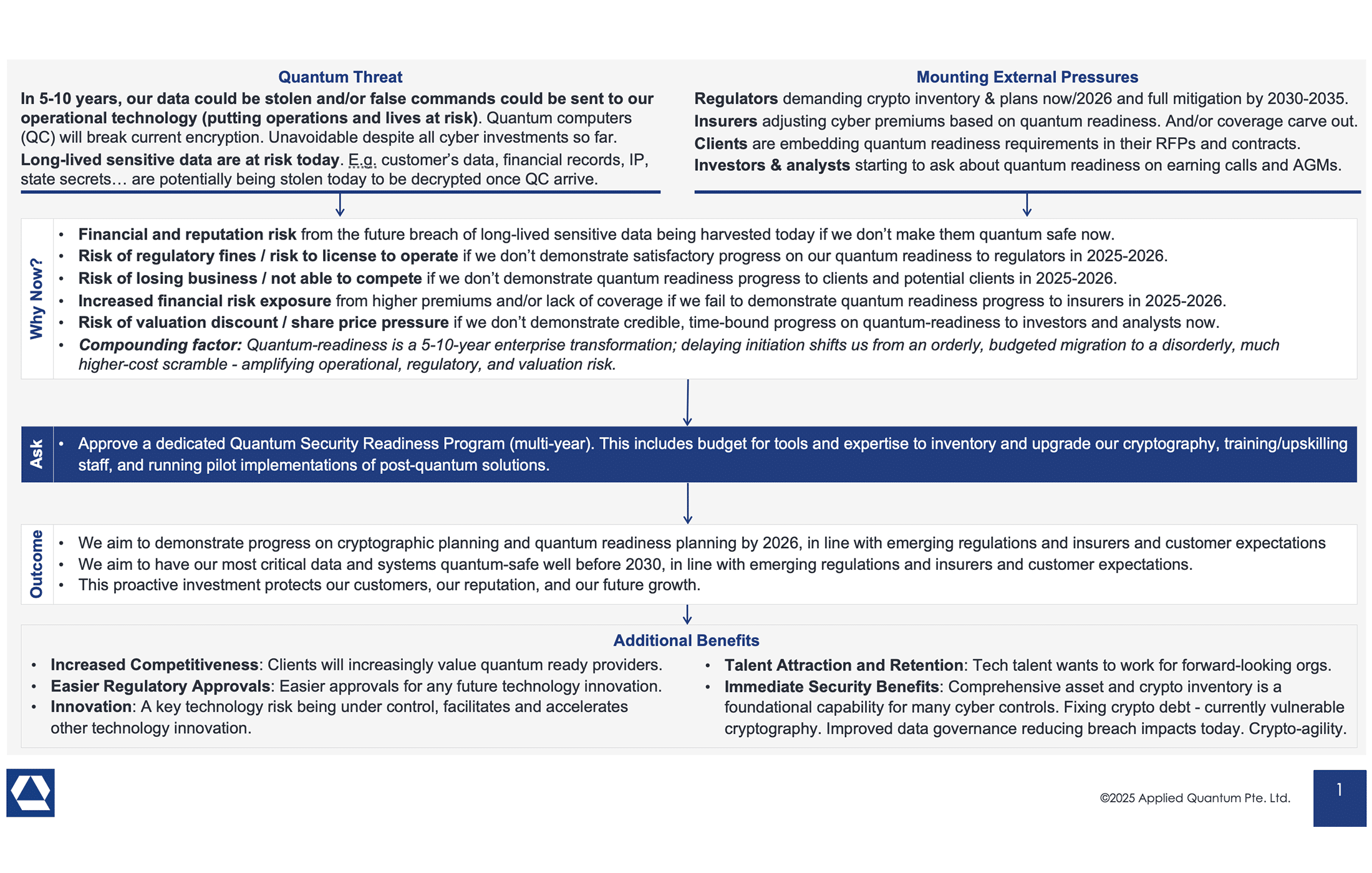
Table of Contents
Introduction
Nearly every CISO I speak with right now is either scoping a quantum‑readiness program or already knee‑deep in one. And the question I’m asked more than any other isn’t about algorithms – it’s, “How do I secure the budget, now?”
This post is my attempt to help all the CISOs. I try to explain, in business terms, why the threat is already on your balance sheet (via harvest‑now‑decrypt‑later), why regulators and sector bodies are setting near‑term expectations, and how insurers, customers, and investors are beginning to price quantum risk into contracts, underwriting, and earnings calls. Beyond compliance, it shows the upside: lower total cost versus last‑minute remediation, stronger customer trust and business continuity, a recruiting edge with top security talent, and immediate hygiene gains from crypto inventory, crypto‑agility, and supply‑chain hardening.
Risk View
The Imminent Quantum Threat: “Harvest Now, Decrypt Later”
Quantum computers capable of breaking today’s encryption may still be years away, but the threat is immediate due to “harvest now, decrypt later” tactics.
In this scheme, adversaries (including nation-states) are intercepting and stockpiling encrypted data today, planning to decrypt it once a powerful quantum computer is available. In other words, any sensitive information that needs to remain confidential for years (financial records, personal data, intellectual property, state secrets) is at risk of exposure in the future if it’s only protected by current encryption.
Security agencies and experts have raised alarms about this risk. The G7 Cyber Expert Group warned in 2024 that threat actors may already be implementing harvest-now-decrypt-later schemes against confidential data.
Likewise, industry analysts note that attackers “can’t afford to wait” – they are grabbing encrypted troves now, betting they can unlock them later. This means the clock is ticking for organizations: even if “Q-Day” (the day quantum cracks encryption) is a decade out, data you secure today could be compromised when that day comes. The only way to truly protect long-lived data is to start deploying quantum-resistant encryption now, before adversaries get their quantum “skeleton key”.
In summary, the quantum threat is urgent and risk-based: we must act on the assumption that a cryptography-breaking breakthrough will eventually happen, and prepare in advance.
Mounting Regulatory & Compliance Pressures (Especially in Finance)
Around the world, governments and regulators aren’t waiting for quantum attacks to happen – they are imposing concrete deadlines to transition to post-quantum cryptography (PQC). A flurry of laws and roadmaps from major economies all converge on roughly 2030-2035 as the timeframe to complete migration to quantum-safe encryption. For example, in the United States a 2022 federal law and White House directives (National Security Memorandum-10) have effectively set 2035 as the deadline for all federal systems to implement quantum-resistant cryptography. Federal agencies are already inventorying their cryptographic systems and drawing up transition plans to meet that mandate.
In the financial sector, regulators are moving even faster. The European Union’s June 2025 Coordinated PQC Transition Roadmap requires critical infrastructure industries (including finance) to complete their post-quantum upgrades by end of 2030 (with broader adoption by 2035). In other words, European banks, payment systems, insurers, and other high-risk financial institutions must be quantum-safe by 2030 – no excuses. By 2026, every EU member state must have a national PQC plan and pilot projects underway, creating near-term milestones.
The U.K.’s National Cyber Security Centre has published similar guidance with key migration steps to hit by 2028 and full completion by 2035. Regulators in other regions (North America, Asia-Pacific) are expected to follow suit or even set tighter schedules.
Sectoral regulators in finance are also sounding the alarm. In a 2024 statement, the G7 Cyber Expert Group (advising finance ministers and central banks) highlighted the risk of quantum attacks to the financial system and explicitly urged institutions to start planning now for quantum-safe encryption. And so did the BIS in July 2025.
Being unprepared for quantum threats could soon mean falling out of compliance with emerging cybersecurity regulations and industry standards. For example, we may see future updates to frameworks (like PCI-DSS for payments or FFIEC guidance for banks) incorporate quantum-resistant requirements. Regulators view quantum readiness not as an optional R&D project but as a necessary component of risk management and operational resilience. Organizations that delay could face enforcement action or liability if an incident occurs.
The message is crystal clear: don’t wait. A wholesale cryptography overhaul takes years, so regulators expect crypto-agility efforts to begin now. Early movers will find the transition less disruptive (and likely less costly) than laggards who procrastinate.
Customers & Vendors: Quantum-Ready or Lose Business
It’s not just governments. Major customers, business partners, and supply chain stakeholders are starting to insist on quantum readiness from the organizations they work with. The most cyber-mature enterprises – large banks, defense contractors, tech giants, etc. – recognize that their security is only as strong as the weakest link. They don’t want a vendor or partner to become the backdoor a quantum-enabled attacker opens. As a result, procurement policies and vendor management are evolving to include post-quantum criteria. Concretely:
- Security Questionnaires: Companies are adding questions like “What is your quantum risk management plan? Are your products and services PQC-ready?” to their vendor risk questionnaires. Industry consortia, such as the Financial Services Information Sharing and Analysis Center (FS-ISAC), have even drafted sample questions to help firms assess each supplier’s post-quantum preparedness. If you’re a vendor and don’t have a good answer, you risk being disqualified or losing deals in competitive bids.
- Contract Clauses: Procurement teams are baking cryptographic agility requirements into new contracts. Many large enterprises (and government customers) now stipulate that vendors must upgrade their products to NIST-approved quantum-safe algorithms by a set date, or be able to operate in hybrid (classical + PQC) modes. In practice, this means if you sell software, hardware, or cloud services, you could be contractually obligated to support quantum-resistant crypto once standards are finalized. Vendors who cannot commit to this may simply be excluded from consideration.
- Future-Proofing Expectations: Clients increasingly demand that any product they buy today can be upgraded easily to PQC tomorrow. Requests for proposal (RFPs) now include language around “crypto-agility” – the ability to swap out cryptographic algorithms without massive re-engineering. Organizations that can demonstrate this flexibility gain a competitive differentiator, because the customer perceives less future risk. As one analysis put it, being quantum-ready is becoming a selling point – if you can’t demonstrate it, don’t be surprised when a client picks a rival that can.
Even if many companies are still in early stages, the tide has turned. Forward-looking CISOs and procurement officers are raising the baseline security requirements for suppliers. This means that being proactive on quantum security now can directly help retain and win customers, whereas ignoring it could soon mean missing out on lucrative partnerships. No one wants to be the vendor that gets tagged as the “quantum risk” in a supply chain and cut out of the network.
In summary, quantum readiness is fast becoming a business necessity – not just for your own security, but as a trust factor in the eyes of clients and partners.
Cyber Insurance is Changing the Game
Another powerful driver for acting now is the evolving stance of the cyber insurance industry. Insurers are in the business of quantifying risk, and they have taken note of quantum computing’s disruptive potential. The last thing insurers want is to cover massive losses from a breach that could have been prevented by timely cryptographic upgrades. As a result, insurance policies and premiums are beginning to reflect quantum risk :
- Coverage Exclusions: Some cyber insurance providers are considering policy carve-outs for quantum-related incidents. For instance, if a company’s data gets decrypted by an adversary using a future quantum computer (i.e. a breach caused by obsolete encryption), the insurer might deny the claim on the grounds that this was an “uninsurable” failure to maintain up-to-date security. We’ve seen analogous moves in the past (e.g. excluding nation-state cyber attacks); quantum vulnerabilities could be next on the exclusion list.
- Premiums & Underwriting: Insurers are starting to treat quantum readiness as a factor in underwriting. Don’t be surprised if your next renewal questionnaire asks whether you’ve begun migrating to PQC or have inventoried your quantum-vulnerable systems. Firms that can answer “yes” – with evidence of real progress – are likely to earn better terms or lower premiums. Those with no plan may face higher premiums or reduced coverage limits. In essence, insurers may reward quantum-ready organizations and penalize laggards for the added risk.
- Industry Warnings: Thought leaders and ratings agencies (like Moody’s) have publicly highlighted that quantum computing could render current encryption obsolete, leading to systemic cyber risks. The scenario of widespread crypto failure is on the radar of insurers as a potential “black swan” event. So, from a board perspective, if we rely on cyber insurance as a safety net, that net may weaken or vanish if we ignore quantum threats. You cannot simply assume “insurance will pay out” if a quantum-enabled breach occurs – insurers might argue that failing to prepare was a form of negligence or lack of due care.
For the CISO, this translates into a clear boardroom message: not preparing for quantum could increase our financial exposure. If certain damages won’t be insured, the organization would have to absorb them. Directors and risk officers should view quantum mitigation as reducing the risk before it materializes, rather than hoping insurance will cover the aftermath.
In short, cyber insurance is incentivizing proactive defense – it’s better (and cheaper) to avoid the quantum breach in the first place than to gamble on an insurance payout that might never come.
Investors and Boards Are Starting to Ask Tough Questions
Beyond customers and insurers, shareholders, analysts, and board directors themselves are waking up to the quantum risk. Over the past year, awareness of the “Q-day” threat has exploded in executive circles. We’ve now seen multiple instances of investors directly inquiring about quantum preparedness:
- Earnings Call Scrutiny: In some recent quarterly earnings calls, CEOs and CFOs of large companies have been put on the spot by analysts about quantum risks. Analysts have essentially asked: “How are you addressing the fact that quantum computers could undermine your security?”. This is a new twist on the standard cybersecurity questions public companies get (e.g. about ransomware defenses). If our leadership doesn’t have a good answer to the quantum question, it could shake investor confidence. Public companies are expected to anticipate emerging risks, and quantum is rapidly moving from sci-fi to a concrete line-item in risk disclosures.
- Boardroom Briefings: Corporate boards are increasingly requesting deep-dive sessions on quantum cybersecurity. Directors don’t necessarily want a physics lesson, but they do want to understand “How serious is the threat, how soon do we need to act, and what is management doing about it?”. I’ve personally been invited to present on this topic to several boards recently, which shows how top-of-mind it’s become. Forward-looking CISOs are proactively educating their boards, emphasizing that quantum risk is ultimately business risk – when Q-Day hits, it’s not just an IT problem, it threatens operations, compliance, and reputation. No CISO wants to be in front of the board after-the-fact explaining why they did nothing about a “ticking time bomb” everyone saw coming.
- Investor Expectations: Institutional investors and regulators (like the SEC) are increasingly focused on cybersecurity resilience as part of good governance. Quantum readiness is joining the list of metrics that signal a well-governed, future-proof company. Just as companies today are expected to have climate risk disclosures or pandemic contingency plans, tomorrow they’ll be expected to have a quantum risk mitigation plan. If two companies are otherwise equal, investors may favor the one better prepared for post-quantum security as the safer long-term bet. Ignoring the quantum issue could soon be seen as a governance lapse, whereas showing leadership here earns credibility with shareholders.
The takeaway is that quantum risk has reached the C-suite and board level discussion. Smart CEOs and CISOs will want to get ahead of it – not just to avoid tough questions, but to demonstrate to investors that the company is on top of emerging threats. By securing budget now and laying out a clear quantum readiness roadmap, management can show foresight and reassure stakeholders that this challenge is being addressed head-on.
Competitive Advantage from Acting Early
Investing in quantum-safe security isn’t just about risk and compliance – it’s also about gaining a strategic edge. There are several competitive benefits for businesses that move early:
Winning Customer Trust and Business
As mentioned, being known as quantum-secure can help retain customers and win new deals. In markets like financial services, clients (and even retail consumers) are becoming aware of the quantum issue. A bank or vendor that can advertise “your data is safe even in the quantum era” immediately stands out. It signals to customers that you are protecting their data for the long haul, which can increase trust and loyalty.
Conversely, if a future quantum-driven breach hits a competitor, you will be in a stronger position to assure customers and regulators that your foresight prevented such an incident. Avoiding the reputational damage of an encryption failure is priceless – continuity of secure operations means continuity of business. Analysts note that a quantum-induced encryption breach would severely impact customer trust and investor confidence in an organization. By acting now to prevent that scenario, you preserve your brand’s integrity.
In short, quantum readiness can be a selling point, showcasing your organization as one that stays ahead of cyber threats to keep stakeholders safe.
Talent Attraction and Retention
Forward-looking projects like quantum security can be a magnet for top cybersecurity and IT talent. Many skilled professionals (especially younger engineers and those passionate about cryptography) want to work on “the next big thing.” If your company is among the first tackling post-quantum implementations, it sends a message that you’re innovative and future-focused. As one CISO put it, the chance to solve cutting-edge challenges “can reinvigorate a team’s sense of purpose.” When an organization announces a project to prototype post-quantum encryption or test new cryptographic tech, the enthusiasts in the team light up – it’s an exciting opportunity to learn and do something “cool”.
I’ve personally seen cyber professionals reach out wanting to join such initiatives, even if they were happy in their current jobs, simply because they crave involvement in this new frontier. From a hiring perspective, being known as a company working on PQC gives you an edge: talented candidates often choose roles not just for salary, but for growth and innovation opportunities. Being able to say “Come work with us – we’re implementing next-gen cryptography and tackling tomorrow’s threats today” is a compelling recruiting pitch. It signals that your security team isn’t stuck firefighting mundane issues, but is actually pushing the envelope.
This helps retain your best people too – involving your current team in quantum readiness efforts keeps them engaged and learning, rather than looking for more exciting work elsewhere. In an industry where burnout is high, giving staff a visionary project can boost morale and loyalty.
Business and Technology Innovation
Embracing quantum-safe practices early can spur broader innovation. It forces organizations to modernize legacy systems, adopt more efficient crypto architectures, and become more agile. Early adopters will have more time to experiment, pilot, and optimize quantum-safe solutions (whether PQC algorithms or quantum key distribution in the future), potentially yielding performance or integration learnings that slower competitors won’t have. Also, by being early, you can help shape standards and best practices, perhaps even influence customers or regulators rather than simply follow them. All of this can translate into a market leadership image – positioning your firm as a tech leader rather than a follower. That kind of reputation can attract partnerships and opportunities that those scrambling at the last minute might miss.
In summary, being proactive about quantum security isn’t just defensive – it’s strategic. It demonstrates to the market, employees, and investors that your organization is forward-looking, which can pay dividends in multiple ways.
“Pay Now or Pay Much More Later”: The Cost of Waiting
One argument that resonates strongly in budget discussions is the cost efficiency of starting now versus the huge costs of scrambling later. Replacing cryptographic systems is a complex, multi-year effort – doing it in a rushed or reactive manner (for example, after a major breach or under a tight regulatory deadline) can be far more expensive and risky than a planned gradual migration. Experts consistently warn that the longer organizations delay, the more they risk a compressed timeline that will strain resources, inflate costs, and increase the chance of mistakes.
An illustrative point came from a U.S. Senate hearing on quantum cybersecurity: “The cost of over-preparing early (by upgrading crypto in advance) is far lower than the cost of reacting too late after a catastrophic breach of our classical encryption.” In plainer terms, investing proactively in the next few years will likely cost only a fraction of what an emergency retrofit or breach recovery would cost later.
Consider the expenses if we had to respond to Q-Day with urgency: emergency consulting fees, expedited hardware replacements, potential system downtime for upgrades, incident response, legal penalties, customer notification and PR damage control, etc. Those far exceed the steady, budgeted cost of a phased migration started today. Furthermore, by acting now, we can spread the investment over multiple budget cycles, pilot solutions to avoid costly missteps, and integrate upgrades with other planned tech refreshes (minimizing duplication of effort). If we wait until the last minute, we lose all those advantages and may have to rip-and-replace systems in a panic – a very expensive proposition.
There’s also a liability and opportunity cost angle. Should a quantum-related breach occur because we delayed, the financial impact would include not just technical recovery but loss of business (customers leaving due to mistrust), regulatory fines for inadequate security, and lawsuits. Board members have a fiduciary duty to consider such foreseeable risks. Quantum risk is a known ticking bomb; failing to address it could even be seen as negligence. On the flip side, any money spent now on mitigation yields immediate security improvements (as we discuss next) in addition to future-proofing, so the ROI is multifaceted.
All things considered, the prudent financial move is to invest in defenses now, rather than pay a ruinous price later.
Immediate Security Benefits of Starting Now
One often overlooked aspect of requesting a quantum security budget is that these projects deliver near-term payoffs for cybersecurity and IT hygiene. In fact, preparing for PQC can be a catalyst to solve lingering security challenges. By funding a “quantum readiness” initiative, we’re not just mitigating a future risk – we’re also going to simultaneously improve our security posture today. You can see more about this in my other post: How CISOs Can Use Quantum Readiness to Secure Bigger Budgets (and Fix Today’s Problems). Key immediate benefits include:
Comprehensive Asset & Crypto Inventory
The first step in any quantum migration is to inventory all your cryptographic assets – you can’t upgrade what you don’t know you have. This means cataloging every system, application, device, certificate, and algorithm in use. Many regulators require this step by 2025-2026 as part of quantum readiness compliance. Undertaking it will finally give us a full map of our IT environment.
Let’s face it, most organizations struggle to maintain a 100% accurate asset inventory; there are always orphaned systems or shadow IT. Quantum readiness gives us the perfect excuse (and budget) to do asset inventory right. We’ll shine a flashlight into every corner of our network and uncover devices or applications that were off the radar.
This immediately reduces risk: you cannot secure what you don’t see. Past studies found a large percentage of security leaders have suffered incidents due to unknown or unmanaged assets in their infrastructure. By discovering these now, we can bring them under management or retire them. Essentially, the quantum project helps kill two birds with one stone: achieve future crypto-agility and attain a complete, up-to-date inventory of our environment, which benefits all of IT and security.
Fixing Weaknesses (“Crypto Debt”)
While documenting our cryptography, we are almost certain to find outdated or misconfigured encryption in our systems. Think of legacy applications using deprecated algorithms (e.g. SHA-1, old SSL/TLS versions), hard-coded credentials, 1024-bit RSA keys that should have been retired, expired certificates, etc. These are vulnerabilities right now, not just in a quantum future.
A PQC readiness assessment will drag these into the light, allowing us to remediate them as part of the program. In essence, it forces us to confront existing crypto-related security holes – what one might call “crypto debt” accumulated over years. Fixing them will harden our defenses against present-day threats (like conventional cyber attacks that could exploit weak encryption or poor key management). One global bank CISO noted that their post-quantum project doubled as a crypto hygiene cleanup – they discovered old self-signed certificates and legacy protocols that were quietly undermining compliance with current standards, and fixed them in the process.
By funding quantum risk mitigation, we essentially get a budget to do a thorough spring cleaning of our crypto infrastructure, which we otherwise might have postponed. That reduces our breach risk immediately.
Building Cryptographic Agility
Migrating to PQC is not a one-time fix; it’s about becoming nimble in the face of changing cryptography. By starting now, we will implement the tools and processes for “crypto-agility” – the ability to swap out cryptographic algorithms and keys quickly across our systems. This involves refactoring systems to support new algorithms, abstracting crypto modules, and avoiding hard-coded dependencies. These practices ensure that next time any algorithm is broken (whether by quantum or a classical attack), we can respond with far less pain.
Leading agencies like NIST and Canada’s CCCS emphasize that cryptographic agility is a best practice for resilience. By investing in quantum-safe upgrades, we’re effectively training our organization to be agile in cybersecurity – an investment that will pay off for any future cryptographic change or mandate, not just quantum. For example, if a new regulation requires migrating from one hash function to another, a crypto-agile enterprise can comply by tweaking configs rather than embarking on a massive overhaul. Thus, this budget helps future-proof our systems in a general sense.
Stronger Vendor and Supply Chain Security
A post-quantum program doesn’t stop at our perimeter – it forces scrutiny of our third-party risk as well. We will need to engage our vendors now about their plans for PQC (e.g. asking cloud providers and software suppliers how they’ll support new algorithms). By doing so, we preemptively inoculate our supply chain against future threats. We’ll quickly find out which partners are forward-thinking and which are “asleep at the wheel”. In fact, our inquiry might spur some vendors into action, improving security for all. Baking PQC requirements into our procurement going forward raises the security baseline of our whole ecosystem.
An added benefit: this initiative will increase cross-department collaboration (IT, security, procurement, legal all working together on contracts and vendor assessments for quantum). That breaks down silos and embeds security deeper into business processes – a cultural win that has positive spillover into other areas (e.g. better communication on software purchases, more security awareness in contract teams).
Improved Data Governance
Quantum risk forces us to ask, “Which data will still be sensitive 5, 10, 20 years from now?” and “Do we really need to keep it that long?”. As we plan PQC upgrades, we’ll conduct a thorough data classification and retention review. Long-term secrets (customer PII, long-lived intellectual property, etc.) will be identified for stronger protection or re-encryption. Simultaneously, we will identify data that no longer needs to be kept and can be securely archived or deleted before Q-Day. Most organizations accumulate far more data than necessary; this is a chance to implement the “clean-up” executives often talk about. Deleting obsolete sensitive records now means even if a quantum adversary shows up later, there’s less data for them to target or decrypt.
Reducing our data footprint also reduces current risk (e.g. less data to be stolen in any breach) and costs (less storage and backup overhead). Every record we securely destroy today is one less liability tomorrow. So the budget for quantum readiness doubles as a budget for better data hygiene and privacy compliance.
To summarize, starting quantum security migration now yields numerous co-benefits: enhanced visibility, elimination of known weaknesses, improved agility, tighter supply chain security, leaner data management – all of which make us safer today. These are compelling side-effects to mention when asking for budget: even if Q-Day is far off, the organization will immediately get stronger and more resilient by investing in this effort.
Conclusion: The Business Case for Quantum Readiness Now
Whether one believes a cryptographically relevant quantum computer will arrive in 5 years or 15, the world around us is not taking chances – and neither should we. Quantum security risk mitigation has shifted from a theoretical tech issue to a concrete business mandate. Regulators have set deadlines; key customers and partners are writing it into contracts; insurers and investors are actively evaluating it. All these external forces have, in effect, started the countdown on us. Waiting until the threat fully materializes will not be an option – by then it would be too late to avoid damage.
From a CISO and business leadership perspective, the ask is clear: we need to secure budget and resources now to begin the multi-year journey of quantum-proofing our organization. This includes funding for risk assessments, cryptographic inventory tools, new encryption software/hardware, staff training or hiring, and pilot projects to start integrating PQC. The investment is justified not only by the avoidance of a potentially catastrophic future breach, but by the immediate gains in cyber hygiene, compliance readiness, and competitive positioning that we’ve outlined. In an urgent, risk-based approach, starting early is the only viable strategy – it spreads out costs, reduces uncertainty, and ensures we won’t be caught unprepared.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.



