Mosca’s Theorem and Post‑Quantum Readiness: A Guide for CISOs
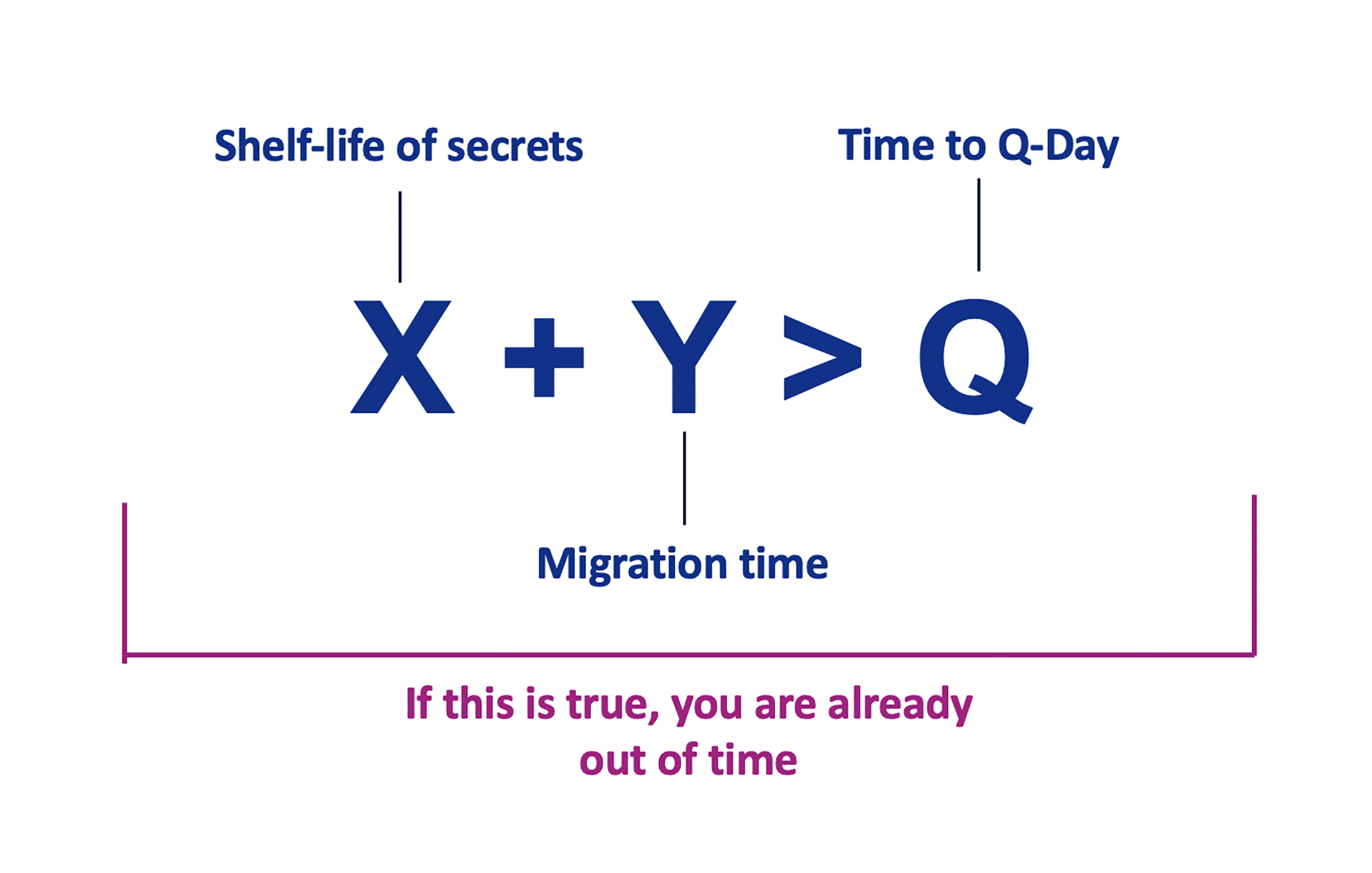
Table of Contents
Introduction
Quantum computing is on the horizon, and with it comes a serious threat to today’s cryptography. Future quantum computers will have the power to break widely used encryption algorithms – particularly our public-key systems (like RSA and ECC) – in a fraction of the time a classical computer would take. This means that the confidentiality and integrity of digital communications, financial transactions, and stored data could be fundamentally undermined once sufficiently powerful quantum machines (“Q-Day”) arrive. Even before that day comes, attackers might be stealing encrypted data now, planning to decrypt it later when quantum capability is available – so-called “harvest now, decrypt later” attacks. In short, the quantum threat isn’t science fiction; it’s a real risk looming over long-term data security.
For CISOs, the quantum threat demands proactive planning. The challenge is twofold: when will quantum attackers emerge, and how long will it take us to prepare defenses? Timing is critical. Upgrading an enterprise’s cryptography to quantum-resistant algorithms is a complex, multi-year effort that requires significant resources and coordination. If organizations wait until quantum computers are already breaking encryption, it will be too late to protect sensitive data that needs to remain confidential for years.
What Is Mosca’s Theorem?
Mosca’s Theorem is a risk framework formulated by cryptography expert Dr. Michele Mosca to help organizations gauge how urgent their post-quantum preparations should be. It is often summarized by the inequality X + Y > Q, where:
- X = the length of time your data must remain secure (the required confidentiality lifespan of the information).
- Y = the time required to migrate or upgrade your cryptographic systems to be quantum-safe (your migration timeline).
- Q = the expected time until quantum attackers can break today’s encryption (the “Z”ero-hour for current cryptography).
In plain terms, Mosca’s Theorem says that if the sum of your migration time and the required security life of your data (X + Y) is greater than the years remaining before quantum computers can crack your encryption (Q), then you’re in trouble. In that scenario, an organization has “already run out of time” – meaning that unless action was started earlier, some sensitive data may become exposed before the new defenses are in place. If X + Y is less than Q, there is still a window to transition, but that window is closing fast as Q approaches.
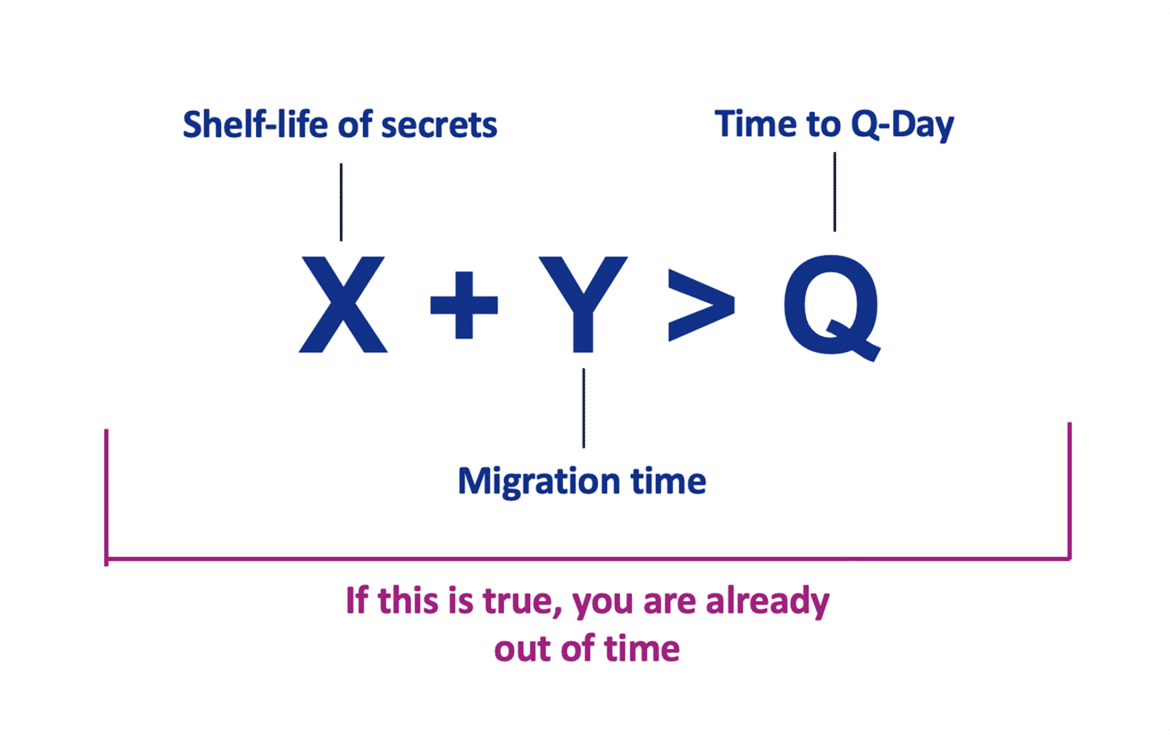
Mosca’s Theorem thus provides a straightforward equation for CISOs to determine when to worry about quantum threats.
Let’s break down the variables with a simple example. Imagine a company needs certain records to stay confidential for at least 10 years (X = 10 years) due to compliance and customer trust. The IT team estimates it will take 4 years to fully replace current cryptographic systems with quantum-resistant solutions across all applications (Y = 4 years). If reliable forecasts say that in about 7 years adversaries will likely have quantum capabilities to crack encryption (Q = 7 years), then plugging these in: X + Y = 14 years, which is much greater than Q = 7 years. According to Mosca’s Theorem, this mismatch means the company cannot afford to wait – if they don’t begin the crypto migration immediately, some of that data could be compromised before the new protections are up. Essentially, whenever X + Y > Q, Mosca’s formula is a warning bell that it’s “time to worry” and act with urgency.
Why It Matters to CISOs
For CISOs, Mosca’s Theorem isn’t just an abstract math formula – it’s a practical tool for risk management in the quantum era. It forces a hard look at three critical timelines: your data’s sensitivity lifespan, your migration project duration, and the quantum threat horizon.
Many organizations will find that certain systems or datasets have longevity requirements that push X + Y into the decade-plus range. For example, the “shelf life” of some security assets can be 5, 10, even 20 years – think of long-term diplomatic secrets, customer financial data, or the root keys in a public key infrastructure that might secure transactions for decades.
Likewise, large enterprises cannot swap out cryptographic infrastructure overnight; a full migration (Y) might easily take several years of planning, procurement, coding, testing, and deployment across numerous applications and devices. In contrast, recent expert surveys and research indicate that the quantum-computing breakthrough could plausibly arrive within the next 10-15 years.
The key insight of Mosca’s Theorem is that these timelines can overlap in dangerous ways. If you have data that needs to stay secure well beyond the moment a quantum attack becomes feasible, you cannot wait until that moment is upon you – you must be quantum-ready before then.
One reason this matters deeply for CISOs is that it helps set priorities and urgency. Not all systems face equal risk from the quantum threat. Mosca’s framework highlights which areas are most critical: those where data confidentiality needs last the longest and where upgrading cryptography will be slow or complex. For instance, a mobile app that only needs to protect data for a few minutes or hours might not be a primary concern, whereas an archival database of personal health records (which must remain private for a lifetime) is a high priority.
Systems embedded in critical infrastructure or IoT devices that can’t be easily updated are another high-risk category – their migration (Y) is lengthy because of hardware or software constraints, and they often handle data or functions that must remain trustworthy for many years (large X).
Mosca’s Theorem gives CISOs a way to identify these ticking time bombs in their enterprise. By calculating or estimating X, Y, and Q for various assets, security leaders can map out a “quantum risk timeline” for each and focus on the ones that are, effectively, quantum-vulnerable sooner.
Another important aspect is communicating risk to stakeholders. The simplicity of X + Y > Q makes it easier to explain the quantum threat in board meetings and strategy sessions. Instead of diving into quantum physics or cryptographic algorithms, CISOs can frame the problem as a timeline collision: “We need our data secure for Y years, it will take X years to adapt our cryptography, but we might only have Q years before attackers have quantum capabilities.” This concrete framing resonates with business executives, who are used to thinking in terms of timelines, project durations, and risk thresholds.
It can be an effective way to justify budget and resources for post-quantum cryptography (PQC) initiatives now, rather than later. And given that while a vast majority of executives acknowledge the quantum threat’s significance, only a fraction have formally incorporated it into their risk management plans, CISOs have a critical role in bridging that gap. Mosca’s Theorem provides a compelling, easy-to-understand argument for why delay is dangerous – and why preparing for quantum is a matter of when not if.
The Problem of “Crypto‑Procrastination”
Despite clear warnings, many organizations are falling into the trap of what we like to call “crypto-procrastination.” This term refers to the tendency to put off dealing with necessary cryptographic upgrades and post-quantum planning – essentially, delaying action because the threat hasn’t yet materialized. It’s an easy habit to slip into: quantum risk feels like tomorrow’s problem, budgets are tight, and there are always more immediate fires to fight. However, crypto-procrastination can be perilous. Every year of delay is effectively one less year to execute what may be the biggest upgrade to cybersecurity in decades. If organizations wait too long, they could face a scenario where the transition to quantum-safe cryptography must be done in a frantic rush, or worse, where the transition simply can’t be completed before attackers break in.
Michele Mosca himself has cautioned that the slow pace of quantum readiness across industries is partly due to this procrastination. He describes it as the habit of “delaying security overhauls because the precise arrival date of the threat is unknown.” In other words, people keep asking “When will quantum day be here?” instead of acting on the assumption it could be sooner than expected. The uncomfortable truth is that we may not get a clear advance warning for “Q-Day.” As Mosca quips, you don’t wait to see a burglar on your lawn before locking your doors – you lock up because even a small chance of a break-in is unacceptable. Likewise, even if there’s, say, a 10% chance that hackers will have quantum decryption capability by the end of next decade, that risk is far too high to ignore. The cost of being caught unprepared could be catastrophic, ranging from the exposure of years’ worth of sensitive data to the collapse of trust in critical digital systems.
Another danger of procrastination is that it compresses the timeline for doing the work. Every year of inaction now means that future implementation tasks will be crammed into a shorter period, potentially compressing future implementation tasks into unrealistically short timeframes. This compression increases the likelihood of mistakes, integration problems, and security gaps when the migration eventually can’t be postponed any longer. Think of it like trying to replace the engines on an airplane while it’s in flight – doing it under urgent, last-minute pressure is not a recipe for success.
Finally, crypto-procrastination ignores the active threat of data being stolen today and exploited tomorrow. As mentioned earlier, adversaries have already been observed engaging in “record now, decrypt later” tactics. They may be hoarding encrypted network traffic, confidential records, or intellectual property right now, betting that within a few years they’ll have the tools (via quantum computing or other breakthroughs) to unlock those secrets. If your organization’s data is among those archives and you haven’t moved to quantum-resistant encryption in time, the horse will be out of the barn – an attacker could decrypt years of your data retroactively.
This is a critical point for CISOs to grasp: some breaches can happen in slow-motion. The damage (data theft) happens now, but the visible impact (decryption of your secrets) might only occur once the quantum capability is available. By procrastinating on post-quantum measures, organizations inadvertently grant attackers a longer window to silently gather encrypted data that will eventually become readable. It’s like knowing a vault’s lock will be picked in a few years – and still continuing to fill the vault with valuables in the meantime. The prudent approach is to assume that anything encrypted with non-quantum-safe algorithms and needing long-term secrecy is already at risk.
In summary, “crypto-procrastination” not only squeezes the time to respond, it also potentially sacrifices the confidentiality of data being protected under outdated encryption. The takeaway for CISOs: don’t wait – the clock is ticking, even if the threat isn’t in the room yet.
In conclusion, the era of quantum computing will rewrite the rules of cybersecurity, but Mosca’s Theorem gives us a valuable head start in rewriting our defenses. CISOs who understand this inequality – X + Y > Q – recognize it as a call to take action before the equation balances against us.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.