All Post-Quantum, PQC Posts
-
Quantum Policy, Standards & Regulation News
Inside ITU’s New Quantum Key Standard (Y.3800)
In late 2019, the International Telecommunication Union (ITU) quietly reached a milestone in cybersecurity: it approved a new standard that could redefine how we secure data in the coming quantum era. The standard, known as ITU-T Recommendation Y.3800, is an “Overview on networks supporting Quantum Key Distribution” - essentially a blueprint for building networks that use the strange laws of quantum physics to protect encryption…
Read More » -
Post-Quantum, PQC, Quantum Security
Challenges of Upgrading to Post-Quantum Cryptography (PQC)
The shift to post-quantum cryptography is not a distant problem but an imminent challenge that requires immediate attention. The quantum threat affects all forms of computing—whether it’s enterprise IT, IoT devices, or personal electronics. Transitioning to quantum-resistant algorithms is a complex, resource-intensive task that demands coordination across the supply chain, extensive security audits, and careful management of performance and cost issues.
Read More » -
Post-Quantum, PQC, Quantum Security
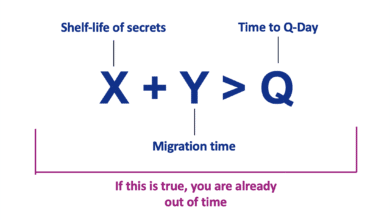
Mosca’s Theorem and Post‑Quantum Readiness: A Guide for CISOs
Mosca’s Theorem is a risk framework formulated to help organizations gauge how urgent their post-quantum preparations should be. It is often summarized by the inequality X + Y > Q, where: X = the length of time your data must remain secure (the required confidentiality lifespan of the information). Y = the time required to migrate or upgrade your cryptographic systems to be quantum-safe (your…
Read More » -
Q-Day
Q-Day (Y2Q) vs. Y2K
In the late 1990s, organizations worldwide poured time and money into exorcising the “millennium bug.” Y2K remediation was a global scramble. That massive effort succeeded: when January 1, 2000 hit, planes didn’t fall from the sky and power grids stayed lit. Ever since, Y2K has been held up as both a model of proactive risk management and, paradoxically, a punchline about overhyped tech doomsaying. Today,…
Read More » -
Quantum Computing
What’s the Deal with Quantum Computing: Simple Introduction
Quantum computing holds the potential to revolutionize fields where classical computers struggle, particularly in areas involving complex quantum systems, large-scale optimization, and cryptography. The power of quantum computing lies in its ability to leverage the principles of quantum mechanics—superposition and entanglement—to perform certain types of calculations much more efficiently than classical computers.
Read More » -
Post-Quantum, PQC, Quantum Security
Introduction to Quantum Random Number Generation (QRNG)
Cryptographic systems rely on the unpredictability and randomness of numbers to secure data. In cryptography, the strength of encryption keys depends on their unpredictability. Unpredictable and truly random numbers—those that remain secure even against extensive computational resources and are completely unknown to adversaries—are among the most essential elements in cryptography and cybersecurity.
Read More » -
Post-Quantum, PQC, Quantum Security
Sign Today, Forge Tomorrow (STFT) or Trust Now, Forge Later (TNFL) Risk
Sign Today, Forge Tomorrow (STFT) or Trust Now, Forge Later (TNFL) is the digital‑signature equivalent of HNDL. Digital signatures underpin everything from software updates and firmware integrity to identity verification and supply‑chain provenance. Today’s signatures are based on RSA or ECDSA, which quantum computers will also break. When that happens, adversaries won’t just read secrets - they will forge signatures at will. The term Sign-Today-Forge-Tomorrow…
Read More » -
Post-Quantum, PQC, Quantum Security
The CRQC Quantum Capability Framework
This guide is a detailed, end‑to‑end map for understanding what it will actually take to reach a cryptographically relevant quantum computer (CRQC), i.e. break RSA-2048 - not just headline qubit counts. A CRQC must meet two conditions: the algorithmic requirements of the target attack and the hardware capabilities needed to execute it fault-tolerantly. The CRQC Quantum Capability Framework organizes these hardware capabilities into nine interdependent…
Read More »