Gartner just put a date on the quantum threat – and it’s sooner than many think
1 Oct 2024 – Gartner just published a clear, plain‑English call to action on post‑quantum cryptography (PQC). The headline message is blunt: “Quantum computing will render traditional cryptography unsafe by 2029.”
As someone who spends a lot of time helping enterprises inventory their crypto, map risks, and plan migrations, I welcome this. Enterprises listen to Gartner; a concrete date tends to galvanize roadmaps, budgets, and executive attention in a way that vague “someday” risks never do. Even better, Gartner’s piece doesn’t hedge on timing for action: begin transitioning now.
A quick read distinguishes between two milestones: “unsafe by 2029” and “fully breakable by 2034.” The latter is the point at which quantum capabilities are expected to directly break today’s asymmetric cryptography; the former signals that security assurance degrades to the point you should not rely on it for confidentiality or authentication. Gartner also foregrounds the harvest‑now, decrypt‑later problem: data stolen today can be decrypted once the capability arrives, which makes “start now” a rational posture even if you’re skeptical about exact dates.
Do I want to see Gartner’s underlying model for 2029/2034? Absolutely. I’d like to know which technical trajectories they weighted most heavily (e.g., error‑correction overheads, algorithmic improvements, realistic device scaling, and the operational maturity needed to attack real‑world protocols) and how they translated that into risk language for the enterprise. The public article states the prediction but doesn’t expose the quantitative spine behind it. If and when they publish more of the methodology, I’ll be first in line to read it. In the meantime, the directional guidance aligns with what many of us have been telling boards and CISOs: plan on PQC as a multi‑year program, not a last‑minute patch.
The article also usefully reframes the migration as harder than Y2K, not because the calendar flips but because cryptography is everywhere – in protocols, applications, embedded systems, and third‑party products – and there’s no single “drop‑in” swap. That means policy, architecture, and engineering discipline, not heroics.
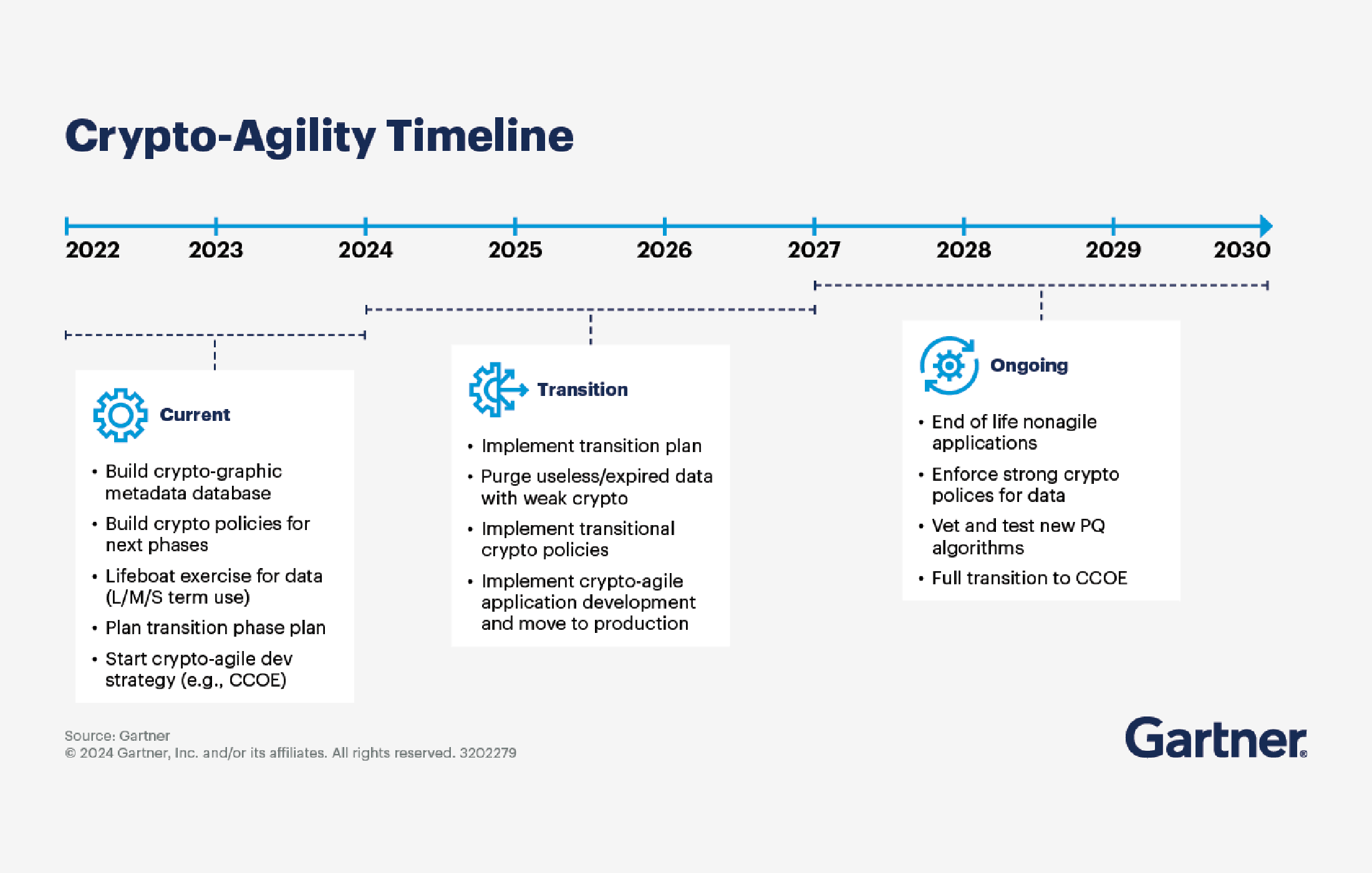
Concretely, Gartner’s recommendations mirror what successful programs are already doing: establish clear policies for algorithm substitution and data retention; build and maintain a cryptographic inventory (including where keys live, how secrets are managed, and which apps depend on which libraries); press vendors for roadmaps; and adopt crypto‑agile development practices so changes can be introduced, tested, and rolled out safely. None of that is controversial, and all of it takes time – which is why starting in 2024/2025 is the difference between an orderly transition and a rushed one.
One more point I’m glad Gartner emphasizes: governments are already moving. Mandates and frameworks are arriving, and many sectors will find that compliance timelines, not just cryptanalytic timelines, drive urgency. If you wait for a formal deadline in your jurisdiction, you’ll be attempting a multi‑year migration on a single‑year clock.
So yes, I’d still like to see the data behind 2029. But I’m happy Gartner is putting a stake in the ground and telling enterprises to begin now. That’s the right message. Treat PQC as a program with governance, inventory, vendor management, and crypto‑agile engineering at its core.
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.