Cyber-Kinetic Security
-
Tangible Threat of Cyber-Kinetic Attacks
Connecting physical objects and processes to the cyber world offers us capabilities that exponentially exceed the expectations of science fiction writers and futurists of past generations. But it also introduces disquieting possibilities. Those possibilities reach beyond cyberspace to threaten the…
Read More » -
Stuxnet and the Birth of Cyber-Kinetic Weapons
Stuxnet was the first true cyber-kinetic weapon, designed to cripple the Iranian – and perhaps also the North Korean – nuclear weapon programs. It succeeded in slowing the Iranian program, although it was discovered before it could deal the program…
Read More » -
Navigating a Safe Course Through Maritime Cyberattacks
The open seas have long attracted those who yearned for adventure. The risk of pitting oneself against a vast and unforgiving sea has tested sailors’ mettle for millennia. It’s not surprising that the maritime industry is one that thrives on…
Read More » -
Our Smart Future and the Threat of Cyber-Kinetic Attacks
A growing number of today’s entertainment options show protagonists battling cyber-attacks that target the systems at the heart of our critical infrastructure whose failure would cripple modern society. It’s easy to watch such shows and pass off their plots as…
Read More » -
History of Cyber-Kinetic Incidents and Research
The fact that cyber-kinetic attacks rarely appear on mainstream news doesn’t mean they don’t happen. They happen more frequently than you would think. Many, for various reasons, aren’t even reported to agencies charged with combatting them. This hinders security experts…
Read More » -
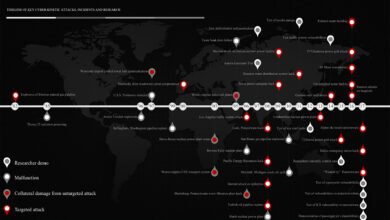
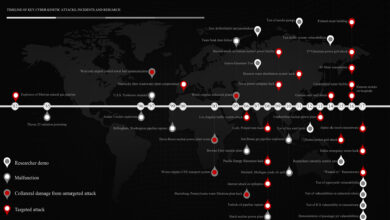
Timeline of Key Cyber-Kinetic Attacks, Incidents & Research
Below is a timeline of key historic cyber-kinetic attacks, system malfunctions and key researcher demos targeting cyber-physical systems (CPS), Internet of Things (IoT) and Industrial Control Systems (ICS) resulting in kinetic impacts in the physical world. I tried to select…
Read More » -
Cybercrime in China – a Growing Threat for the Chinese Economy
Western publications often picture the People’s Democratic Republic of China (hereafter China) as the world’s chief propagator of cyberattacks. But the picture is much more complex than such broad-brush claims suggest. Few Westerners realize that China and its neighbours in…
Read More » -
When Hackers Threaten your Life – Cyber-Kinetic Risks
The attacker stepped out from behind a hedge in the upper-class suburban neighborhood, being careful to stay in the shadows. Across the street, the last lights shining through the windows of the house had just flickered out. She tugged the…
Read More » -
Human Zombification as an Information Security Threat
China and Russia share an information security doctrine, one that is significantly different from Euro-Atlantic doctrines. In the Chino-Russian model of information space a discussion about population zombification does happen and it fits squarely within the domain of information security.…
Read More » -
Emerging Tech Security Guidelines, Frameworks, Standards
Below is my attempt to list of all published 5G, IoT and “Smart Everything”-related security guidelines, frameworks and standards. If you are aware of additional entries that should be here, please let me know at [email protected]
Read More » -
The World of Cyber-Physical Systems & Rising Cyber-Kinetic Risks
We live in a world in which the way we observe and control it is radically changing. Increasingly, we interact with physical objects through the filter of what computational systems embedded in them tell us, and we adjust them based…
Read More » -
Cyber War – scaremongering or reality?
“Cyber war” is a term that is in recent days used so liberally that people may often wonder if these words are as menacing as they sound or used only as a tool to incite fear as a way to…
Read More » -
The Decline of Real Penetration Testing
As the leader of Cyber Agency, one of the largest penetration testing and red teaming specialist outfis, I have a bone to pick with where our industry is headed. Back in the late 90s and early 2000s, "pentesting" actually meant…
Read More » -
Testing AI in Defense – A New Kind of Security Challenge
Looking back at our engagement, I'm concerned that the pace of AI adoption in military will overtake our abilities to validate and verify such systems. If AI systems continue proving valuable, there is nothing that will stop their adoption, but…
Read More » -
Polymorphic Viruses: The Shape-Shifting Malware Menace
Polymorphic viruses represent a turning point in malware history. These shape-shifting programs have shown that malicious code can be made highly adaptable, challenging the very foundations of signature-based security. We’ve examined how polymorphic malware works - using encryption, mutation engines,…
Read More »