Latest Quantum Industry News
China Releases Freely Downloadable Quantum Operating System
China's Origin Quantum Computing Technology Co. has made its quantum operating system, Origin Pilot, available for free public download - a move that multiple sources describe as the first time a quantum computer OS has been offered for local deployment anywhere in the world. The release, announced February 26 through the Anhui Quantum Computing Engineering Research Center and widely covered ...
The White House Just Released Its New National Cyber Strategy. It’s Not a Strategy.
7 Mar 2026 - On Friday afternoon - the traditional Washington burial ground for news you'd rather not have scrutinized - the White House released "President Trump's Cyber Strategy for America," the administration's long-delayed national cybersecurity strategy document. Originally expected in January, the strategy outlines six policy pillars that will ostensibly guide the nation's cybersecurity posture going forward. The document ...
SCSP Launches Bipartisan Commission on U.S. Quantum Primacy
The Special Competitive Studies Project (SCSP) has launched the Commission on U.S. Quantum Primacy (CUSP), a new bipartisan body designed to produce a national strategy for keeping the United States ahead in quantum technologies. SCSP frames the effort not as a narrow science-policy exercise, but as a broader push to connect quantum innovation with national security, economic strength, and long-term ...
Switzerland Just Published the Quietest Quantum Strategy in Europe. It Might Be the Smartest.
The Swiss Quantum Commission just released Switzerland's first comprehensive quantum strategy. For a national quantum strategy, it didn't arrive with the usual fanfare we got used to. No press conference headlined by a prime minister. No headline-grabbing pledge of tens of billions in public funding. No promise to build the world's first fault-tolerant quantum computer by a suspiciously specific date ...
The “Cybersecurity Apocalypse in 2026” and the Jesse–Victor–Gharabaghi (JVG) Algorithm: Why This Claim Doesn’t Hold Up
A preprint manuscript (ID: 202510.1649) titled “A Novel Hybrid Quantum Circuit for Integer Factorization: End-to-End Evaluation in Simulation and Real Quantum Hardware” was published on the Preprints.org server. Authored by researchers affiliated with the Advanced Quantum Technologies Institute (AQTI), the paper introduces the "Jesse–Victor–Gharabaghi (JVG) algorithm" - a hybrid classical-quantum approach to integer factorization that proposes replacing the Quantum Fourier Transform ...
Google’s Merkle Tree (MTC) Gambit to Quantum-Proof HTTPS
Google will not put post-quantum signatures into traditional X.509 certificates for Chrome. Instead, the company announced in February 2026 a fundamentally different architecture - Merkle Tree Certificates (MTCs) - that shrinks quantum-resistant TLS authentication data from roughly 14,700 bytes down to as little as 736 bytes, making post-quantum HTTPS potentially smaller than today's classical certificate chains. The approach, developed jointly ...
No, the “Pinnacle Architecture” Is Not Bringing Q-Day Closer 2-5 Years (but It Is Credible Research)
Since the preprint paper of The Pinnacle Architecture preprint hit and its Quantum Insider coverage ran, my phone has been ringing off the hook. The question behind most of those calls is simple: does this mean RSA is suddenly in imminent trouble? Is it true that this paper brought the Q-Day closer 2-5 years? (Who said that?!?)... The short answer is NO - not ...
The EU Just Proposed Including Post-Quantum Cryptography (PQC) in NIS2
On 20 January 2026, the European Commission published COM(2026) 13 final - a proposed directive amending NIS2 as part of a broader cybersecurity simplification package tied to the upcoming Cybersecurity Act 2. The proposal covers a range of updates: streamlining scope definitions, simplifying cross-border supervision, introducing ransomware reporting requirements, and enabling cyber posture certification as a compliance tool. But buried ...
China Just Pushed Device-Independent QKD (DI-QKD) to 100 Kilometres
A team at the University of Science and Technology of China (USTC) published a paper in Science that quietly redrew the map of what device-independent quantum key distribution (DI-QKD) can do. Led by Bo-Wei Lu, Chao-Wei Yang, Run-Qi Wang, Xiao-Hui Bao, and the ever-present Jian-Wei Pan - the physicist sometimes called China's quantum communications supremo - the experiment demonstrated DI-QKD ...
India’s Task Force Releases Quantum‑Safe Roadmap with 2027–2029 Migration Timeline for CII
India’s Department of Science and Technology (DST) published the “Implementation of Quantum Safe Ecosystem in India – Report of the Task Force.” This report, produced by a national Task Force under DST, lays out a strategic roadmap for transitioning India’s digital infrastructure to quantum-resistant security. The Task Force was chaired by Dr. Rajkumar Upadhyay (CEO of C-DOT) and convened experts ...
Hong Kong’s HKMA Launches Quantum Preparedness Index to Safeguard Finance
Hong Kong’s central bank unveils a “Quantum Preparedness Index” to gauge how ready its banks are for the quantum computing era, underscoring a global push among regulators to future-proof financial security. Hong Kong’s de facto central bank, the Hong Kong Monetary Authority (HKMA), has announced the launch of a Quantum Preparedness Index (QPI) as part of its new Fintech Promotion ...
CISA Draws the Line: The Product Category Advisory & The End of Legacy Procurement
The Cybersecurity and Infrastructure Security Agency (CISA) released a definitive advisory titled "Product Categories for Technologies Use Post-Quantum Cryptography Standards." This document, mandated by Executive Order 14306 (June 2025), fundamentally alters the procurement landscape for the United States federal government and, by extension, the global technology supply chain. The advisory bifurcates the Information Technology marketplace into two distinct classifications: "Widely Available" PQC ...
Citi’s Quantum Threat Report: The Trillion-Dollar Security Race in Focus
The Citi Institute - a research arm of global banking giant Citigroup - published a stark warning titled “Quantum Threat: The Trillion-Dollar Security Race Is On.” In unequivocal terms, Citi’s analysts predict that within the next decade quantum computers are likely to become powerful enough to break widely used public-key encryption. They caution that the economic and geopolitical fallout of ...
G7’s Post‑Quantum Roadmap: Preparing the Financial Sector for a Quantum-Resilient Future
The G7 Cyber Expert Group (CEG) - an international team of cybersecurity authorities co-chaired by the U.S. Treasury and the Bank of England - issued a landmark roadmap for the financial sector’s transition to post-quantum cryptography. This high-level plan, formally titled “Advancing a Coordinated Roadmap for the Transition to Post‑Quantum Cryptography in the Financial Sector,” is aimed at banks, financial ...
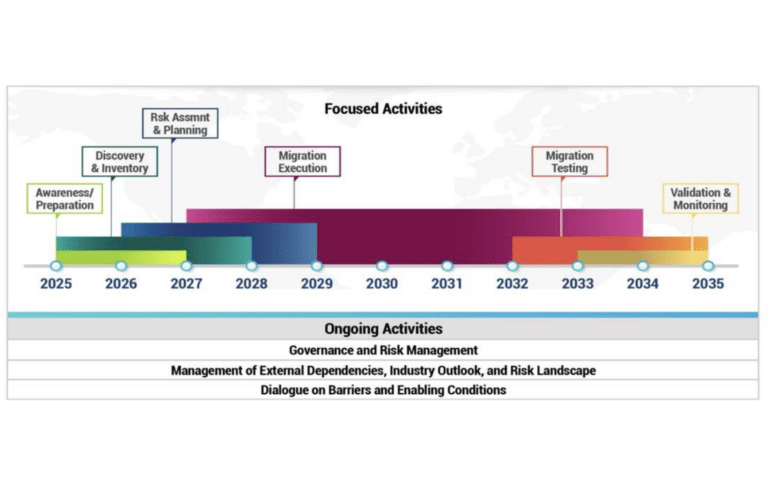
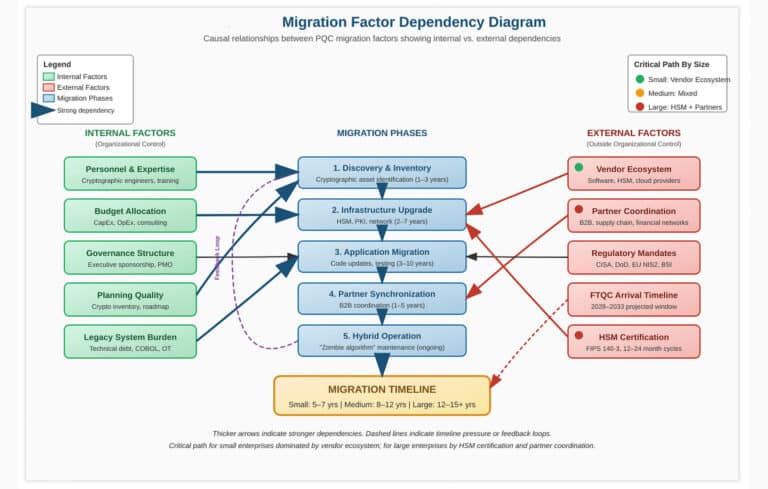
Enterprise PQC Migration: New Study Predicts 5–15+ Year Timelines
A new peer-reviewed study titled "Enterprise Migration to Post-Quantum Cryptography: Timeline Analysis and Strategic Frameworks" by independent researcher Robert Campbell has been published in the open-access journal Computers (MDPI). This paper provides one of the most comprehensive analyses to date of how long it will take enterprises to fully migrate their cryptographic systems to post-quantum cryptography (PQC). The findings are ...
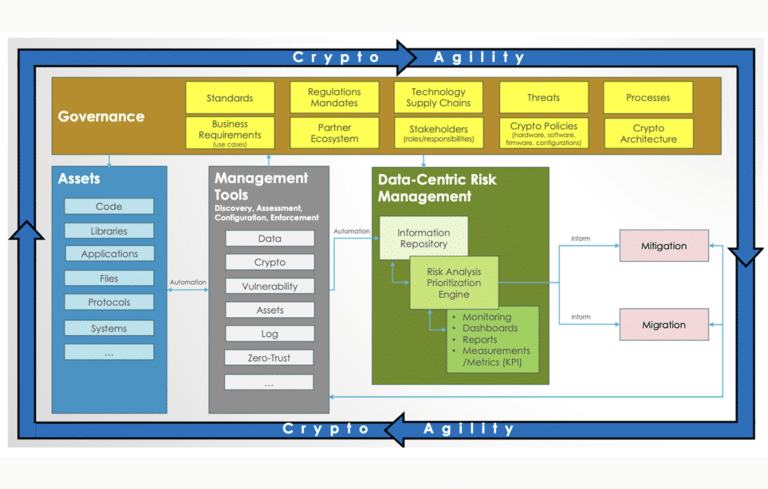
Crypto Agility Goes from Buzzword to Blueprint – NIST Releases “Considerations for Achieving Crypto Agility”
NIST published the final version of the Cybersecurity White Paper (CSWP) 39 – “Considerations for Achieving Crypto Agility: Strategies and Practices.” CSWP 39 elevates cryptographic agility from an oft-cited buzzword to a design imperative for both government and industry. The message is clear: organizations must be able to adapt their cryptography on the fly without breaking systems, treating agility as ...
BIS Project Leap Phase 2 – PQC in Real-World Payment Systems
The Bank for International Settlements (BIS) and the Eurosystem published the results of Project Leap Phase 2, a massive technical trial testing PQC on the TARGET2 payment system (the Real-Time Gross Settlement system for the Euro). The project involved the Banque de France, Deutsche Bundesbank, the Bank of Italy, and Swift. The headline finding was a success: the consortium proved they ...
QuantWare’s “10,000‑qubit chip” headline: a real scaling bet – and why it still doesn’t mean Q‑Day
Dutch startup QuantWare has announced VIO-40K™, a new 3D packaging architecture designed to build superconducting quantum processors with up to 10,000 qubits on a single device. This represents roughly a 100× increase over the scale of today’s largest superconducting chips. The VIO-40K approach uses a stack of chiplets - multiple layers of quantum chips and interposer modules - to deliver ...