The book explores intricate interconnectedness of the cyber and physical worlds. As our interactions with physical objects increasingly rely on embedded computational systems, we unlock capabilities that surpass even the most ambitious predictions of past futurists. However, this fusion also introduces profound vulnerabilities.
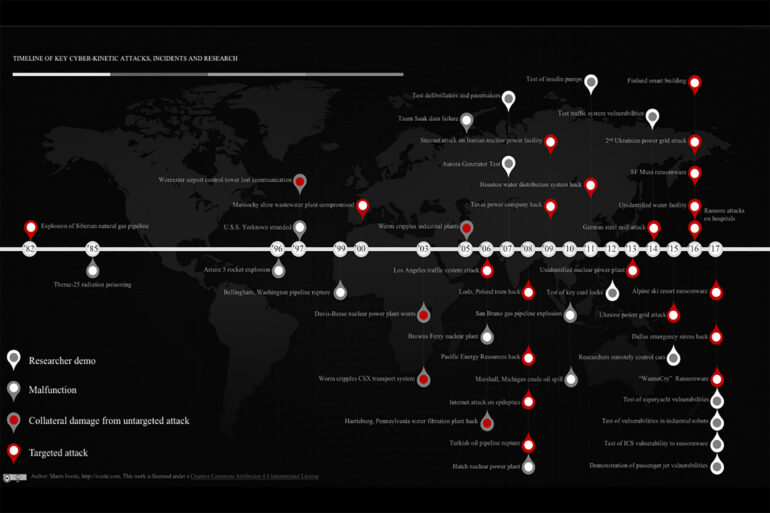
The book describes in detail over 40 real-life cyber-kinetic incidents – cybersecurity incidents that resulted in injuries or fatalities. The book explores the potential threats of our cyber-connected world, reevaluates our current cybersecurity approaches, and offers strategies for risk reduction and mitigation in the face of cyber-kinetic attacks.
Completed in 2017, “Cyber-Kinetic Security” by Marin Ivezic was withdrawn from publication due to organizations impacted by the incidents mentioned in the book retracted their initial approval, choosing to keep the the incidents confidential.
While complying with the request, I firmly believe that keeping such information hidden is not beneficial. Sharing anonymized details of real-life incidents is crucial for raising awareness and imparting lessons learned. This can help other organizations prevent similar attacks.
Articles that follow are adapted from non-controversial book chapters.