All 5G Security & mIoT Security Posts
-
5G Security
Open RAN May Be the Future of 5G, but Can We Keep It Secure?
It’s been a year of contradictions for the telecommunications industry. Like most sectors, it has been heavily impacted by the consequences of the Covid-19 pandemic, with a slowdown in global 5G roll-outs being a notable result. Geopolitical conflicts have continued to muddy the market, with governments playing a more active role than ever in setting telecoms-centred policy. At the same time, however, the air is…
Read More » -
5G Security
5G in Manufacturing – 5G and Time Sensitive Networking (TSN) for Industrial Automation
In the recent report by IHS Markit – “The 5G Economy – How 5G will contribute to the global economy” – researchers claimed that manufacturing will garner almost $4.7 trillion in sales enablement by 2035. Or 36% of the $13.2 trillion total opportunity of 5G by 2035. Manufacturing will be by far the largest industry beyond mobile to be impacted by 5G. In the manufacturing…
Read More » -
5G Security
Cybersecurity and Safety in the 5G-Enabled Smart-Everything World
Neil Harbisson calls himself a cyborg. Without the antenna implanted in his skull, he would not be able to see colour of any kind. Born with achromatopsia, a condition of total colourblindness that affects 1 in every 30 000 people, Harbisson’s physical faculties are augmented by cyber technology to grant him access to a life of greater meaning and satisfaction. As technological evolution leads to…
Read More » -
5G Security
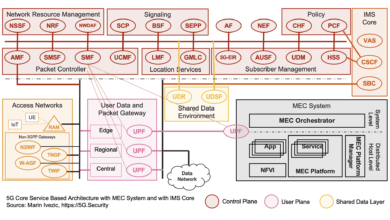
Introduction to 5G Core Service-Based Architecture (SBA) Components
The interest in 5G and mIoT is exploding. It’s exciting to see so many IT and cybersecurity professionals in my network trying to learn more about 5G and related technologies. In addition to my usual articles about the societal impacts of these innovations, I’ll start a series of articles introducing key 5G and mIoT technology concepts. Before we move on to technical aspects of 5G…
Read More » -
5G Security
Smart Home / Smart Building Connectivity Options and Their Cybersecurity
In a recent session on smart building cybersecurity, a student cheekily asked me “How did we ever connect anything before 5G?” At that moment I realized I might have been overdoing my 5G cheerleading recently. To atone, here are the key performance and cybersecurity attributes of the most commonly used connectivity technologies in smart home / smart building use cases… And 5G. If you thought…
Read More » -
5G Security
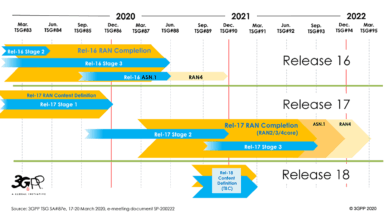
Introduction to 3GPP and 3GPP 5G Releases 15, 16 and 17
In a major milestone for 5G, 3GPP finalized the Release 16 in July – its second set of specifications for 5G New Radio (NR) technology. As a second article in my series of 5G 101 articles, this is a good opportunity to review the 3GPP process and major 5G-related technical specification releases. As well as to clarify some misconceptions about the 5G development process. This…
Read More » -
5G Security
Does the positive review of Huawei UDG source code quality mean that Huawei 5G is secure and reliable?
No, no it doesn’t. Huawei’s code might as well be extremely secure. Their code is certainly the most scrutinized. But the recent UDG source code review is not an evidence of security. ERNW, an independent IT security service provider in Germany, recently performed a technical review / audit of Huawei’s Unified Distributed Gateway (UDG) source code. Huawei made the summary report available here [PDF]. The…
Read More » -
5G Security
Will Telcos Lose the Edge Computing Battle as Well?
For many end-users of today’s communications technology, the cloud is a somewhat mystical concept, a digital equivalent of aether. Most think of it as a formless abstraction “up there” when, in fact, the cloud is rooted in the ground. Or the seabed. Despite rapid advances in satellite connection, almost all intercontinental data transfer that takes place every second of the day occurs via hundreds of…
Read More »