How CISOs Can Use Quantum Readiness to Secure Bigger Budgets (and Fix Today’s Problems)

Table of Contents
Introduction
Talking with the CISOs in my network, I keep hearing the same laments as I’ve been hearing for decades- only now they seem to be louder than ever. From chronic understaffing to new regulatory pressures and AI adoption. I wrote more about that here: “Why Would Anyone Want to Be a CISO Anymore? (Discussion)“. So when I suggest adding quantum readiness to their to‑do list – something many still perceive as tomorrow’s problem – the reaction is predictable: hair‑pulling for those few CISOs who still have any left. How can they prioritize quantum resistance today when they’re already drowning in urgent issues? I can relate – I was in their shoes recently. In the current cybersecurity chaos, it’s hard to get excited about cryptography that won’t be cracked until some future quantum computer arrives.
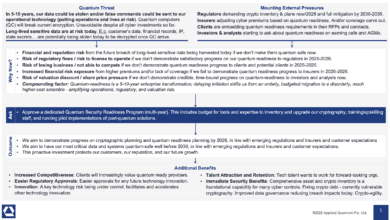
I will, as I often do, remind that the quantum threat is no longer a distant theory – it’s gaining on us, “harvest now, decrypt later” and “trust now, forge later” are today problems, and regulators increasingly want to see concrete progress within months, not years. I’ll take one chapter to sound the alarm bells, but then I want to turn it around to positives. Framed correctly and executed well, a quantum‑readiness program can unlock bigger budgets for CISOs and deliver very real benefits today, way before a cryptoanalytically relevant quantum computer (CRQC) ever comes online.
Quantum Threat: Closer Than It Appears
Tomorrow’s problems have a funny way of becoming today’s crisis if you ignore them long enough. Quantum threat is already becoming a crisis situation if you haven’t started your quantum readiness program yet. If many of us are correct, useful quantum computers might arrive already by 2030, but a quantum readiness program in a large enterprise could easily take 5-10 years. So yes, many organizations are already late at the start, and quantum readiness should be treated as a crisis.
It’s not just me and my peers, top scientists and government agencies now openly warn that we may have less than 5–7 years before quantum attacks become feasible. Countries are taking notice: the EU’s new roadmap published last week urges all member states to begin PQC transitions by 2026 and mandates critical infrastructure be quantum-safe by end of 2030. Similarly, Canada’s federal government requires all high-priority systems to adopt post-quantum encryption by 2031 and they published their requirements on the same day as EU. Many other countries isssued similar requirements. In short, regulators worldwide are moving up deadlines.
Yet despite these warnings, most organizations are far behind. A recent ISACA poll found 62% of security professionals are worried about quantum threats, but only 5% say it’s a high priority for their organization, and only another 5% have even begun planning a quantum-safe strategy. This complacency is setting the stage for potential chaos.
Not just because of the lack of preparation for the Q-Day, but because the threat is present already today. Adversaries are not idly waiting – they’re actively harvesting encrypted data now, to decrypt later when quantum capability arrives. And are potentially harvesting certificates for “trust now, forge later“. Sensitive customer records, intellectual property, emails – anything stolen today can be stockpiled in the hope of one day unscrambling it when a CRQC comes online. This tactic means the quantum risk is effectively already here.
Turning a Burden into an Opportunity
But here’s the encouraging part: quantum readiness, if approached smartly, can be a blessing in disguise for CISOs. The key point is that quantum readiness, to a large extent, relies on the same fundamental cybersecurity hygiene measures you’ve always needed. With regulators and governments increasingly scrutinizing quantum preparedness, CISOs now have a great opportunity to secure dedicated funding to properly address foundational cyber hygiene tasks as a part of specially funded quantum readiness programs, and potentially even freeing up funds from their existing budgets in the process.
Emerging Regulations: Quantum Compliance = Board-Level Priority
One big reason quantum readiness won’t stay “tomorrow’s problem” is the regulatory drumbeat getting louder every day. And if there’s one thing that reliably loosens purse strings in the boardroom, it’s a compliance requirement backed by law or high-level policy.
What does this mean for a CISO? If you do business with the government or in regulated industries like finance or healthcare, get ready for trickle-down compliance. Regulators and auditors (and insurers, and clients…) will soon start asking, “What’s your PQC migration plan? Where are your quantum-vulnerable cryptographic systems? Show us your CBOM (Cryptographic Bill of Material).”
The upshot is that as quantum risk has leapt from theoretical to practical, CISOs will find receptive ears in the boardroom. When you can say, “By investing in quantum resilience, we’re meeting regulatory requirements head-on,” boards listen. No one wants to be caught flat-footed by a new law or an examiner’s question they can’t answer. Funding for compliance initiatives – especially ones framed as future-proofing critical infrastructure – tends to be approved even in tight budgets.
In short, quantum readiness is quickly becoming synonymous with compliance readiness, and that secures the executive mandate and budget you need.
Asset Discovery: The Cybersecurity Foundation That Finally Gets Funded
Before you even start tackling cryptographic inventory, you need to know what assets you have and where they are. That means doing a thorough discovery of everything connected to your network – not just servers and laptops, but all the “hidden” devices too: IoT sensors in the building, OT systems on the factory floor, cloud VMs, rogue Wi-Fi gadgets, shadow IT, you name it. This isn’t new advice; it’s basic cyber hygiene. In fact, the very first of the CIS Critical Security Controls is to inventory and track all enterprise assets (end-user devices, network gear, mobile, IoT, servers, even cloud) so you “accurately know the totality of assets that need to be monitored and protected”. The reason is obvious: you can’t defend or upgrade what you don’t know exists.
Yet in practice, almost no CISO has a 100% handle on this. Even when they think they do. Every organization tries – they spin up CMDB projects, buy fancy asset discovery tools, run network scans – but it’s never properly budgeted and staffed, and it’s a moving target. Budgets are approved only for the next shiny discovery tool that promises to discover all your assets – but they never do. Business units add devices without telling IT, legacy systems linger, and new acquisitions bring in unknown assets. One 2023 survey even found that while 94% of IT leaders claimed to have a “live view” of all devices, nearly half were still tracking assets in spreadsheets – a recipe for blind spots and false confidence. Long story short, getting a truly comprehensive asset inventory has been frustratingly elusive for most security teams.
Quantum readiness can finally change that. It gives you the perfect catalyst (and excuse) to do asset inventory right. Why? Because before you can map out all your cryptographic algorithms, you first have to map out the systems and devices using those algorithms. PQC migration prep essentially forces you to shine a flashlight into every corner of your IT and OT estate. And here’s the opportunity: you can now justify budget and resources for this foundational task under the banner of “quantum resilience and compliance.” Unlike past asset inventory efforts that came out of your standard operating budget (and often got shelved when funds ran tight), this time you can say, “We need to discover all assets as a prerequisite for PQC compliance and risk reduction.” That tends to get board-level attention. It means fresh funding, executive backing, and cross-department cooperation that you might not get for routine cyber hygiene work. And if you already had some budget allotted for asset discovery in your regular roadmap, great – now you might free up those funds for other uses, since the quantum initiative will cover a chunk of it. Essentially, quantum readiness projects let you kill two birds with one stone: achieve your post-quantum goals and finally attain a complete, living inventory of your environment.
The benefits of nailing down your asset inventory go well beyond quantum cryptography. First, you’ll almost certainly uncover surprises – orphaned machines, forgotten IoT devices, shadow IT databases – some of which could be security ticking bombs. (We regularly find all kind of devices with live network connection and default credentials, or even dual-homed, completely unbeknownst to the security team, until an inventory sweep found it.) Identifying and rectifying these blind spots immediately reduces your attack surface. Remember, you can’t secure what you can’t see, and unknown assets are a notorious source of breaches. In fact, nearly 73% of security leaders admit they’ve experienced incidents because some asset in their infrastructure was unmanaged or simply unknown. Once you have a solid inventory, all your other security functions get a boost. Vulnerability management can ensure no device is left unpatched. Incident responders know exactly what systems are in play during an investigation. SOC monitoring can cover every network segment where devices reside. Even IT operations benefit – you can manage upgrades and decommission obsolete gear more systematically. Fundamentally, you’re establishing visibility and control that make your entire security program more effective.
Inventory and Visibility: Immediate Wins from PQC Migration Prep
The first step in any PQC migration is taking a comprehensive inventory of your cryptographic assets and algorithms. (Asset discovery mentioned above could be considered a subset of this step). Cryptographic inventory is highlighted as the first step in virtually every government requirement or a guideline issued recently. (Most of them require you to complete this step by 2026!)
You need to map out every system, application, and device in your enterprise that uses encryption or digital signatures, and document what cryptography it’s using (algorithms, key lengths, certificates, etc.) This might sound tedious – and it is – but guess what? It’s one of the best things you can do for your security posture right now.
Why? Most organizations have never done a thorough crypto inventory before. Over years, companies layer new applications, inherit legacy systems, outsource here, acquire a company there – and crypto implementations proliferate like wildflowers (or weeds). I’ve seen companies surprised to discover mission-critical applications still using 20-year-old encryption libraries, or rogue VPN appliances using default credentials, simply because no one had a full list of “where our encryption lives.” By forcing you to shine a flashlight into every corner of your IT estate, the PQC inventory exercise provides an invaluable visibility boost. It’s like a full network and software asset inventory, but with a focus on encryption. And you can’t secure what you don’t see.
Think of it as a full-body scan for your IT security: maybe you’ll find that an internal admin tool is still using an outdated TLS 1.0 protocol, or that a database is using a weak hashing algorithm for passwords. These are the kinds of issues that attackers could exploit long before a quantum computer arrives. By doing a PQC-focused inventory now, you’re likely to uncover and fix such weaknesses as a byproduct. One global bank CISO told me their post-quantum readiness project doubled as a crypto hygiene cleanup – they discovered old self-signed certificates and legacy algorithms that were quietly undermining their compliance with current standards.
So, undertaking a cryptographic inventory gives you an immediate boost in security visibility and hygiene. Even before any new quantum-resistant algorithms are deployed.
Fixing Today’s Cryptographic Vulnerabilities (Cleaning up the “Crypto Debt”)
Continuing from the inventory comes another near-term benefit: finding and fixing cryptographic vulnerabilities you already have. Almost every mature organization has some amount of crypto debt – outdated or misconfigured encryption lurking in the tech stack. Common examples include: use of deprecated algorithms like SHA-1 or MD5, RSA keys that are too short, expired or self-signed certificates, unsupported cryptographic libraries, or even hard-coded secrets in legacy applications. These are security holes today, not tomorrow.
What you uncover through your cryptographic inventory efforts, can be alarming, but it’s a huge opportunity to improve your cyber hygiene. For instance, you might discover that a third-party service your HR department uses is still relying on an insecure cipher suite for its HTTPS connections. Or you might realize that an internal tool never got the memo to disable TLS 1.0, putting internal data at risk. During normal operations, these issues often go unnoticed. But in preparing for PQC, they surface – and you can drive immediate remediation.
In essence, quantum readiness initiatives force you to confront your existing crypto weaknesses. The process will raise questions like: “Why do our IoT devices still use RSA-1024 certificates – who’s maintaining that? Should we upgrade them now?” or “We found a partner integration using an old VPN with pre-shared keys – that’s a problem.” By addressing these, you reduce your attack surface against current threats. You’re less likely to fall victim to already known exploits.
I’ll give a concrete anecdote: One organization I advised discovered during their crypto inventory that a critical file-transfer server was using an out-of-the-box configuration with outdated algorithms. This server had passed routine IT audits for years, because the audits checked general patching and configs but not crypto specifics. It took the PQC project to put it under a microscope. The team promptly updated the configurations – closing a hole that, frankly, could have been exploited by a moderately skilled hacker with no quantum computer needed. These are the kind of immediate fixes that quantum readiness drives.
Regulators like the U.S. NSA have noted this side effect too. The NSA’s guidance for national security systems (NSS) not only pushes post-quantum algorithms by 2035, but also calls for eliminating weak crypto in the near term (e.g. requiring quantum-resistant solutions for things like software signing and web traffic by 2025). The thinking is clear: the journey to PQC naturally involves upgrading and patching your cryptography, which yields a safer environment right now.
Crypto-Agility: Future-Proofing for Any New Threat
One term you’ll hear a lot in these discussions is “crypto-agility.” This isn’t just buzzword bingo – it’s a crucial capability for security longevity. Crypto-agility means having systems and processes that can swiftly swap out cryptographic algorithms and protocols without needing a complete overhaul. Think of it as modular encryption: if one component becomes unsafe or non-compliant, you can drop in a new one.
Why is this important beyond the quantum scenario? Because cryptography doesn’t stand still. We’ve seen algorithms that were once trusted become obsolete in a matter of years (for example, RC4, DES, SHA-1 – all strong in their heyday, all now retired due to weaknesses). New compliance requirements also emerge (like mandates for longer keys or newer protocols). If your organization is crypto-agile, you can handle these changes with far less pain. If not, even a minor crypto change can be like pulling a thread in a sweater – things unravel.
Preparing for PQC inherently pushes you to build crypto-agility. You’ll be refactoring systems to support new quantum-resistant algorithms. During that process, smart teams will set up their systems to be flexible: perhaps implementing a hybrid crypto approach (using classical and post-quantum algorithms together initially), abstracting cryptographic implementations behind interfaces, and generally avoiding hard-coded crypto choices in software. All of these practices ensure that next time an algorithm needs replacement – whether due to a new quantum breakthrough or a traditional vulnerability – you can do it quickly through configuration or routine updates.
Leading security agencies emphasize this. The Canadian Centre for Cyber Security, for example, explicitly states that “cryptographic agility is a best practice” so that systems remain secure even if algorithms are broken, and it hinges on maintaining an inventory and interchangeable crypto components. In other words, be ready to pivot when cryptography changes. By investing in quantum readiness, you’re essentially training your organization in agility. You establish processes to update crypto libraries, manage keys at scale, test new algorithms in your environment, and coordinate these changes across different products and teams. Those processes won’t just apply to quantum algorithms – they’ll make you nimble for any cryptographic curveball.
This pays compliance dividends too. Consider future privacy regulations or industry standards that might require new cryptography (we’ve already seen PCI and others push for more modern TLS configurations), or from one hash function to another. With crypto-agility, such mandates are less scary – you can comply by tweaking settings rather than rewriting code for months. Your security infrastructure becomes more resilient to change, which is a hallmark of mature cybersecurity programs.
Supply Chain Security Improvements
It’s not just your own systems that need quantum-hardening – it’s your vendors’ as well. A post-quantum program forces you to extend your security scrutiny beyond your walls and into your supply chain. Think of all the third-party software, cloud services, and vendors that handle your data or connect to your network. If even one critical supplier lags in upgrading their cryptography, that weak link could undermine everyone. CISOs who start engaging vendors now about their PQC roadmap are effectively inoculating their ecosystem against future threats. In fact, U.S. agencies like CISA explicitly advise organizations to assess their supply chain’s quantum readiness and to proactively engage technology vendors on their plans and responsibilities for PQC. By asking partners “What’s your post-quantum migration plan?” you’re not only protecting your own flank – you’re also sending a message that security is a non-negotiable criteria for doing business.
The immediate payoff here is twofold. First, you’re likely to discover which of your vendors are forward-thinking and which are asleep at the wheel. Some suppliers may not even be aware of looming quantum requirements – your inquiry can spur them to start their own crypto-upgrade (a rising tide lifts all boats). We’ve seen cases where a PQC readiness review prompted a vendor to patch a weak encryption module years before it might otherwise have been caught. Second, by baking PQC criteria into procurement and contracts going forward, you fundamentally raise the security baseline of your supply chain.
There’s a softer, but important and related benefit too: running a quantum preparedness program forces greater collaboration between departments. To tackle vendor risk, your security team will need to work closely with procurement, legal, and enterprise risk teams – perhaps even forming a “quantum-ready” task force. This cross-functional teamwork pays dividends immediately. It breaks security out of its silo and embeds it into vendor management and business processes. The security team gains a clearer view of upcoming tech purchases, and the procurement/legal teams become more fluent in cybersecurity matters. That improved communication and security-by-design mindset will help with many other initiatives, not just PQC.
Data Governance: Protecting Long-Lived Secrets (and Cleaning House)
Another often overlooked perk of quantum readiness is the chance to radically improve your data hygiene. Post-quantum planning isn’t only about algorithms; it starts with asking “Which data do we truly need to keep secure for decades?” This inevitably leads to a thorough data classification and retention review. You’ll map out which datasets are sensitive and have long-term confidentiality needs – and which do not. Most organizations have never scrutinized their information in this way. As a result, they accumulate years of archives and backups without a strong business case. Quantum risk forces the issue: if you’re holding data that will still be sensitive in 5, 10, or 20 years, you either need to protect it with quantum-resistant crypto or consider disposing of it before Q-day. It’s a fantastic motivator to finally implement that “data lifecycle management” initiative that your execs keep talking about. In fact, experts recommend prioritizing “long-lived data” in your PQC plans – focusing your encryption upgrades on information that truly must remain confidential beyond the 2020. By the same token, you’ll identify data that has passed its useful life. Why spend time and money re-encrypting a trove of outdated customer records or old intellectual property that you no longer need or are past regulatory retention requirements? Far better to securely archive or delete it now.
Clearing out obsolete data isn’t just good prep for the quantum era – it dramatically reduces your current risk and costs. We’ve seen security teams seize this moment to delete aging encryption keys, old databases, and miscellaneous files that had been lurking in backups – drastically shrinking the footprint of sensitive data that could be stolen or ransomed. Even regulated data that must be kept (say, for compliance) can often be minimized; for instance, by securely removing personal identifiers or aggregating records. Every record you sanitize or shred today is one less thing that could be decrypted by an adversary tomorrow.
Attracting and Retaining Top Cyber Talent with Future-Focused Work
Here’s a benefit many overlook: working on forward-looking projects like quantum security can be a huge morale and talent attraction boost for your cybersecurity team. Let’s face it – one reason burnout is high in our field is that too many skilled practitioners spend their days doing unglamorous tasks (chasing phishing emails, responding to compliance checklists, etc.). The chance to tackle cutting-edge challenges can reinvigorate a team’s sense of purpose. I’ve witnessed it firsthand: when a CISO announces an initiative to, say, prototype post-quantum encryption in the corporate network, suddenly the crypto enthusiasts and ambitious engineers in the org light up. It’s an opportunity to learn new skills and work on something “cool.” Since I started Applied Quantum, I am being contacted daily by cyber professionals in my network and my former colleagues interested in joining me even though they are currently happy in their current roles – they just want to jump on a chance of doing something new and cool.
In a competitive job market for cybersecurity, being an organization that invests in innovative projects can set you apart. Talented professionals often choose roles not just for salary, but for growth and interest. If you can say, “Come work with us – we’re implementing next-gen cryptography and tackling tomorrow’s threats today,” that’s a compelling pitch. It signals that your security program isn’t stuck in reactive mode, but rather pushing the envelope. Many top young analysts and engineers want exposure to things like quantum-safe crypto, AI in security, cloud-native security architectures, etc.
Moreover, involving your current team in these efforts helps with retention. It breaks up the monotony of day-to-day operations. Imagine telling your security architects and engineers that they get 20% of their time this quarter to experiment with integrating a post-quantum library into an internal application, or to run a lab test of quantum-resistant VPN software. This isn’t a distraction – it’s training. You’re investing in your people’s skills. Surveys of cybersecurity professionals frequently show that lack of advancement or training is a top reason for job dissatisfaction. On the flip side, organizations that invest in staff development and interesting projects have better retention rates. (In fact, 72% of organizations in a recent (ISC)² survey said they invest in staff training to strengthen their teams, underscoring how important growth opportunities are.)
So, by being proactive about quantum security, you send a message internally and externally: we are a cyber leader, and our people get to work on important, novel challenges. That draws in high-caliber talent who might otherwise gravitate to more “exciting” tech companies or research roles. And it keeps your existing talent engaged. One CISO told me that their post-quantum task force became a hot ticket – folks from different IT and engineering groups volunteered to join because it was seen as an elite, forward-thinking initiative. In an era where skilled cyber personnel are hard to hire and harder to keep, this is a non-trivial benefit.
Boosting Stakeholder Confidence and Reputation
Last but certainly not least, demonstrating quantum readiness bolsters confidence among all your stakeholders – from customers and business partners to regulators and investors. It shows that your organization is not just securing the present, but also anticipating the future. In the world of corporate risk (and especially in industries like finance, healthcare, and critical infrastructure), this kind of foresight and diligence is a reputational asset.
Think about the due diligence questionnaires or security assessments your enterprise goes through. Today, they might not have a section on “quantum-resistant cryptography” – but soon they very well could. Even now, savvy partners might ask how you protect data against long-term threats. If you can answer: “We have a roadmap in place for post-quantum cryptography and are already inventorying and strengthening our cryptographic controls,” that instills confidence. It tells them you’re not just ticking the basic compliance boxes, but truly aiming to safeguard data for its entire lifecycle. This is especially pertinent for data with long confidentiality needs – for example, healthcare records or trade secrets that need to stay secret for 10+ years. As we discussed above.
From a regulator’s viewpoint, being quantum-ready puts you in a proactive light. If an examiner or audit team brings up PQC (and they increasingly will), you’ll be ready to show them plans, policies, and progress. That can only help your compliance profile. Even if no one explicitly asks, including a note about quantum preparedness in your annual security report or ESG (Environmental, Social, Governance) disclosures can be a differentiator. It’s evidence of good governance. Just as companies that adopted cloud security early or embraced zero-trust architectures earned a certain cachet for being ahead of the curve, so too will those who can say they are “quantum-resistant” in their security posture.
And let’s not forget the board and executive stakeholders. Cybersecurity is a regular board agenda item now, and board members fret about systemic risks and the next big threat around the corner. When you brief them that you’ve initiated a quantum readiness program – aligned with NIST guidelines, supporting compliance, improving your security fundamentals – it provides reassurance that the security team is thinking long-term. It flips the narrative from always reacting (breach, patch, repeat) to strategically preparing. I’ve seen board directors visibly relax when we explain how an organization is preparing for quantum risks: “Okay, good, one less black swan to worry about.” In some cases, it even becomes a bragging point to shareholders or customers (“Our company is one of the first in our sector to implement quantum-safe encryption…”).
In short, quantum readiness is a trust signal.
Conclusion
Yes, quantum computing capable of cracking today’s encryption is still on the horizon. We don’t know exactly if it’s 4 years, 7 years, or more before “Q-day” arrives. But preparing for it is not an exercise in science fiction – it’s a very practical program that yields benefits immediately. Regulators are pushing us all in this direction, which means boards are willing to fund it. The journey forces you to finally catalog your cryptographic assets and clean up long-standing weaknesses, improving your security posture right now. It builds agility so you can handle any crypto curveballs the future throws. It energizes your team and attracts talent by giving them something exciting to work on. And it demonstrates to the world that your organization is on top of emerging threats, thereby inspiring confidence.
(I explore these points, and much more, in my upcoming book, “Practical Quantum Resistance”. If you’re looking for clear strategies and actionable guidance to get your organization quantum-ready, head over to QuantumResistance.com and sign up to stay in the loop!)
Quantum Upside & Quantum Risk - Handled
My company - Applied Quantum - helps governments, enterprises, and investors prepare for both the upside and the risk of quantum technologies. We deliver concise board and investor briefings; demystify quantum computing, sensing, and communications; craft national and corporate strategies to capture advantage; and turn plans into delivery. We help you mitigate the quantum risk by executing crypto‑inventory, crypto‑agility implementation, PQC migration, and broader defenses against the quantum threat. We run vendor due diligence, proof‑of‑value pilots, standards and policy alignment, workforce training, and procurement support, then oversee implementation across your organization. Contact me if you want help.